Botnet Attacks are becoming increasingly popular among Cyber Criminals due to their ability to Infiltrate almost any Internet-Connected Device.
Today, botnets pose one of the biggest threat to Cyber Security Systems as their Use ranges from Activism to Sponsored Disruption…
Where most botnet attacks are simply profit-based.
Botnets are commonly used as tools to influence elections by Spread Fake News and to Mine Cryptocurrencies.
So, Don’t you think – It is important to Prevent Botnet Attacks…
But before that, you must know what is a Botnet? | How it Works? | Botnet Types etc…
What is a Botnet Malware?
A botnet is a group of internet-connected devices which have been infected with malware used to control them from a remote location by a malicious user.
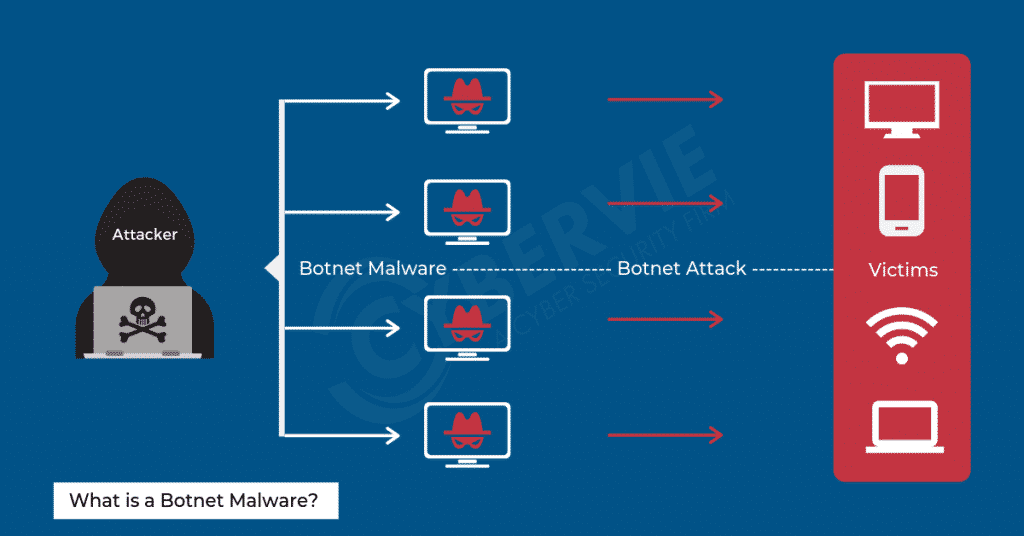
Botnet Malware is dangerous to both Corporations and Consumers as they can be designed for various tasks such as…
- Deploying malware
- Sending spam
- Stealing personal data
- Defrauding advertisers
- DoS attacks
Depending on the method of control, the attacker or “bot herder” can amplify the damage they cause.
Some botnet malware is instructed to take total control of the target device. Whereas other malware runs silently as a background process while waiting silently for instructions from the bot herder.
The impact size of the botnet attack depends on the size of the botnet.
So botnet attackers use self-propagating botnets that recruit additional devices as bots through a variety of channels.
The devices targeted for these seek-and-infect missions are the ones that lack OS Updates or Antivirus Software.
IoT devices such as Security Cameras and Refrigerators are particularly Vulnerable for Botnet Attacks.
As they are relatively New and their Security is not taken as seriously as that of Computing Devices.
How do Botnets work?
Botnet Control Structure is a major requirement for a sophisticated botnet attack is the ability of a botnet to receive updated instructions from the bot herder.
The botnet attacker can Change targeted IP addresses, Start or Terminate a Botnet Attack and, Other Customised Actions.
The designs to accomplish these tasks varies…
But, the structure is designed in a way that gives the botnet attacker as much control as possible.
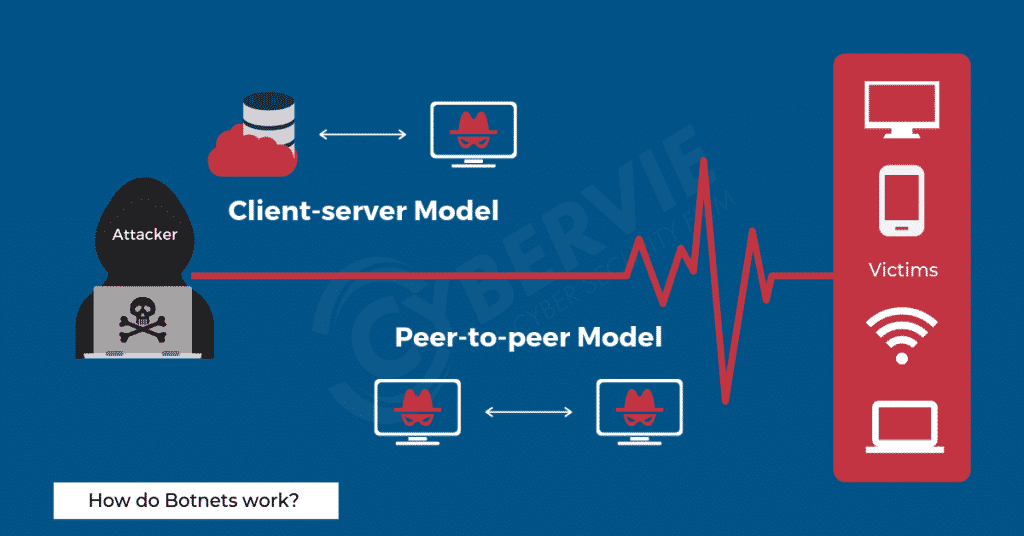
Client-server Model
This model mimics the traditional network setup style. Here each individual machine is connected to one main server in order to access information.
Each bot connects to a command and control server which are used by the botmaster to modify the source code and relay instructions to each client device.
Popular centralized botnet topologies include Star Network Topology, Multi-Server Network Topology and, Hierarchical Network Topology.
Although this model works well for taking and maintaining control over the botnet, only the server needs to be disrupted to kill the botnet.
Sophisticated attackers are moving to the P2P model to prevent this vulnerability of disruption via a single or a few points of failure.
Peer-to-peer Model
The decentralized peer-to-peer structure is being used recently to overcome the shortcomings of the client-server model.
These botnets work hand-in-hand with their neighbouring nodes were each infected device functions as a client as well as a server.
Each bot connects to a limited number of trusted devices with which they communicate and update malware.
This army is harder to disrupt as tracking a single server isn’t enough to stop the botnet attack.
P2P botnets are typically encrypted so that access is limited and the bot herder does not lose control of the botnets.
List of Some Major Botnets?
As of 2019, there are many types of botnets influenced by Cyber Criminals. But we have listed out few Major Botnets you must know about…
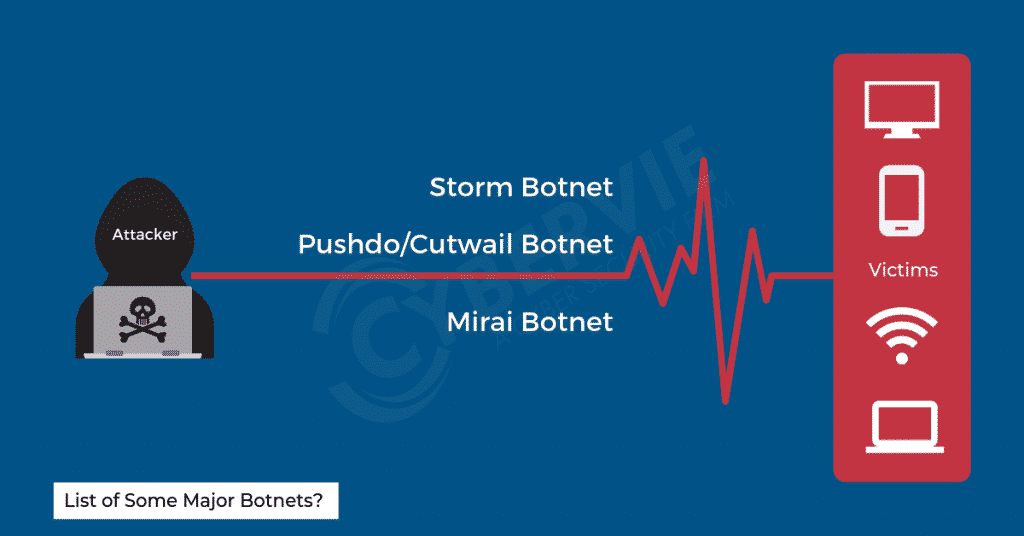
Storm Botnet
It was one of the first known peer-to-peer botnets. That is, it was among the first to be controlled by several different servers that were linked by a Trojan horse spread by email spam.
The network was tremendous and could be rented out to any criminal willing to pay for it on the dark web.
Because of this, Storm was involved in a wide range of criminal activities, from Botnet DDoS attacks to identity theft and was reportedly powerful enough to force entire countries off the Internet.
Some of Storm botnet servers were shut down in 2008, and today it is thought to be more or less inactive.
Pushdo/Cutwail Botnet
Founded around 2007, Cutwail is a botnet mostly involved in sending spam e-mails.
The bot comprised of 1.5 million infected machines at the time and typically infects computers running Microsoft Windows by way of a Trojan component called Pushdo.
Even after an attempted takedown by the FBI and other law enforcement agencies in 2014.
The Pushdo/Cutwail botnet remains active affecting computer users in over 50 countries and available for rent today.
Mirai Botnet
It was behind a massive distributed botnet denial of service (DDoS) attack in 2016 that left much of the internet inaccessible on the U.S, east coast.
The most surprising thing is that the purpose of this botnet was to only gain an edge in Minecraft…
But the attack expanded and affected the Internet in such a huge region.
Mirai Botnets was one of the most notable botnets as it was the first major botnet to infect insecure IoT devices.
At its peak, the worm infected over 600,000 devices.
Types of Botnet Attacks?
Botnets can be used for various types of botnet attacks. But are most commonly used in the attack strategies that require traffic volume as botnets are comprised of tens of thousands of zombie computers.
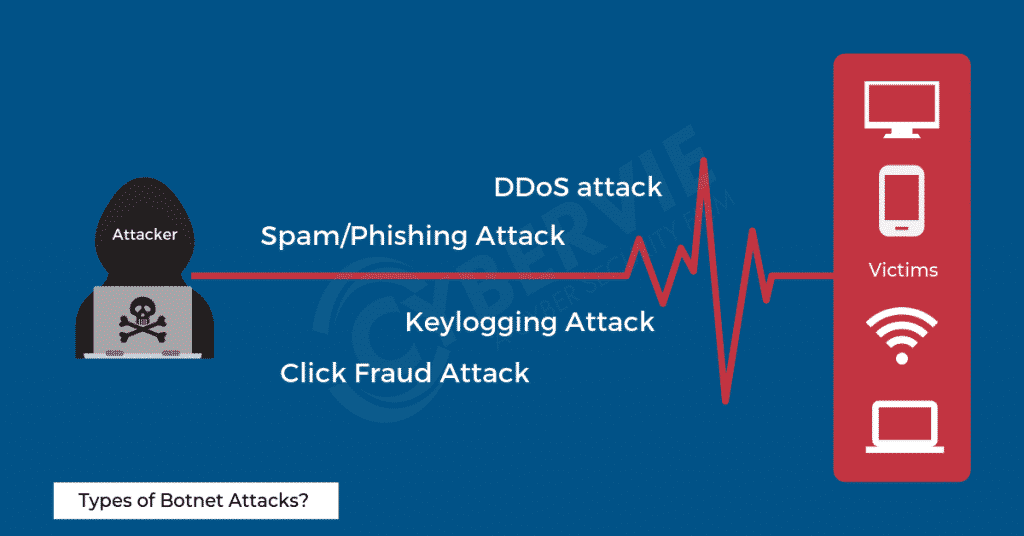
Botnet DDoS attack
A Denial of Service attack is the most common use of botnets…
DDoS Botnet – Attacks a network or a computer system for the purpose of obstructing service through the loss of connectivity or consumption of the victim network’s bandwidth.
And, overloading of the resources of the victim’s computer system.
By sending a large number of requests which is more than the capacity of the system…
And hence results in the genuine requests being pushed to the end of the request processing queue.
Many game servers are constantly under botnet DDoS attacks on individual players are becoming increasingly common.
Botnet DDoS attacks are sometimes also used to damage or take down a competitor’s website or for petty revenge against organizations.
When a user tries to access the website, the browser sends a request to the host server and waits for a short duration.
If no response is received, the browser displays an error message saying that the page is not available or request timed out.
This error message does not do a good job of describing the actual error. You may not even be aware that your own network or the website server is under a Botnet DDoS attack.
Botnet Spam/Phishing Attack
Botnets are used to harvest email addresses or to send massive amounts of spam or phishing emails.
These emails pretend to be a legitimate company and usually contain a link. This takes you to a cloned copy of their login page which is actually owned by the Botnet Attacker.
When a user falls into this trap and enters their details on this page, the credentials are automatically sent to the Botnet Attacker’s device.
This technique is called phishing which is now executed through botnets as they provide anonymity to the malicious user.
As for spam emails, botnets are preferred due to their large volume.
Other than spam, bots also look for login credentials and other sensitive data by acting as packet sniffers to find and intercept sensitive data passing through an infected machine.
Both herders use this confidential information for their personal gain and evil intentions.
Botnet Keylogging Attack
If the compromised machine uses encrypted communication channels (e.g. HTTPS or POP3S).
Then just sniffing the network packets on the victim’s computer won’t let the bots harvest any substantial information since the appropriate key to decrypt the packets is missing.
Botnet Attackers have adapted to this problem by making use of a keylogger program in the infected machines.
Which makes it easy for the bot owner to retrieve sensitive data.
They can implement a filtering mechanism to only record the key sequences near specific keywords such as Gmail.
The scale of this procedure is daunting when you take into consideration that there are probably thousands of compromised devices which have a keylogger running on them.
Botnet Click Fraud Attack
A pay-per-click system is one where advertisers are charged a tiny amount each time someone clicks on their advertisement on a web page or each time the advertisement is loaded into a browser.
Therefore this system is open to abuse and botnets can be used for financial gain by automating clicks.
It is impossible to tell whether a user clicked on the link genuinely to know more about the advert or was tricked into clicking it.
The IP address can’t be used to differentiate either as the statement of activity can be used to show different addresses for every event.
So in botnet click fraud attack, a zombie army is used to show thousands of visitors to a page in order to artificially increase the click counter of an advertisement.
Another major use is to spread new bots in the network…
This is achieved very easily by tricking the user to download and execute a file via FTP, HTTP or Email etc.
Botnet Attacks Prevention Tips?
Unfortunately, these Prevention Tips Cannot assure the Complete Protection against all types of Botnet Attacks…
But helps to prevent most Individual Computers or Devices from Basic Botnet Attacks.
Tip 01 – Monitor Updates on Regular Basis
Fortunately, most OS and browser companies are aware of the menace of the bots. Thus they keep shutting down the security weaknesses constantly by providing security updates and patches.
So make sure you upgrade your Software and Operating System to avoid becoming a victim of Botnet Attack.
Tip 02 – Be Alert with Emails from Suspicious or Unknown Sources
Bots often use contact lists to Compose Spam with Infect Emails.
Don’t download any files attached to speculative emails that come from people who you don’t know.
If a known person sends an unusual attachment or link, confirm the authenticity of the email before opening or downloading anything.
Tip 03 – Download Torrents and PDFs with Caution
Botnets use P2P networks and file-sharing services to infect computers.
Scan any downloads before executing the files as the free online PDFs may be infected that can slip a Trojan into your computer.
Find safer alternatives for transferring files and never download files that don’t have recognizable file extensions.
Tip 04 – Enable Licenced Firewall and Antivirus
Botnets sneak into all types of devices. Therefore look for a licenced antivirus that protects all your devices and not just your computer.
Usually operating systems have a free-of-cost integrated firewall and antivirus systems that are aimed at keeping your computer free of Trojans and zombie control programs.
Don’t turn them off just to download certain free and attractive software off the internet. You could be inviting trojans and malware into your device.
Summary
Botnets can be created with ease, which made these botnet attacks more accessible and that too at a dirt-cheap price.
It is necessary to be vigilant and protect all your internet-connected devices from becoming a bot herder’s puppet.
The range and number of botnet infections are increasing. It is important that every organization should monitor their networks periodically in order to prevent botnet attacks.
Advanced Support on Web Application or Network Security
Individual users also need to become a part of the solution if they want to keep accessing their favourite websites and play online games.
Hope you Prevent becoming a Victim of a Botnet Attack Today…
Do we miss any of the Botnet Attack Prevention Tip – Kindly Comment Below to Help the Fellow Citizens!








