Burp Suite is a Penetration Tester’s go-to tool when performing a Web Penetration test. It’s a java executable and hence is cross-platform. It establishes its usefulness by providing various hacking tools that impeccably work together throughout the entire Scanning and Testing process. This blog post will take you through a quick run-through of the features provided by Burp by providing a demo on DVWA(Damn Vulnerable Web App).

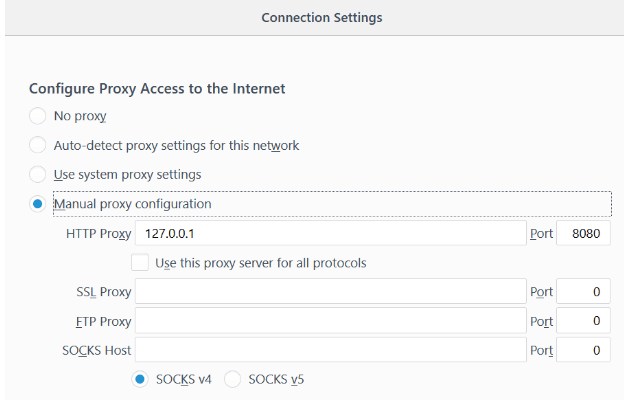
The main characteristic of Burp is that it acts as an intercepting proxy, that is it intercepts the traffic between a web browser and web server. In order to intercept HTTP requests, the first step is to configure Firefox to use a manual proxy configuration(found under options>general settings>network proxy)
The default setting is localhost 127.0.0.1 and port 8080
Now open up Burp Suite and choose to create a temporary project
The interface shows up as follows
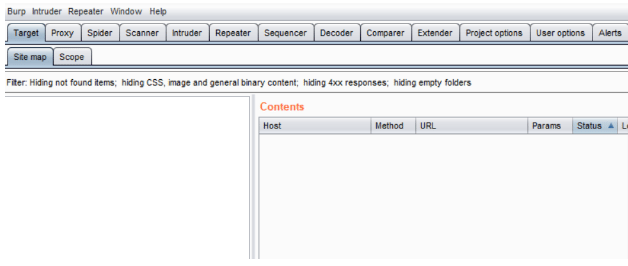
The various features of Burp include proxy, spider, intruder, repeater, sequencer, decoder and comparer. Here I’ll explain the basic use of these functionalities.
Scope and Intercept
Initially set the Network proxy on firefox to ‘None’ and open up DVWA in the browser. You can see the login page with two input fields ‘Username’ and ‘Password’. Log in using the credentials: admin, password
BY default, security is set to impossible. Select DVWA security and change it to ‘low’.
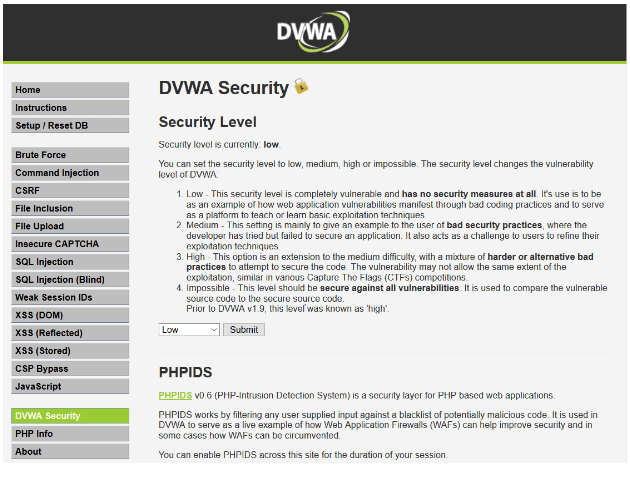
Go to the Brute Force option and add the url to target scope as you’ll be using other web applications of Firefox so Burp knows that DVWA is the site it has to stay within the scope of and it doesn’t end up sending any malicious traffic to websites that one isn’t authorized to test.
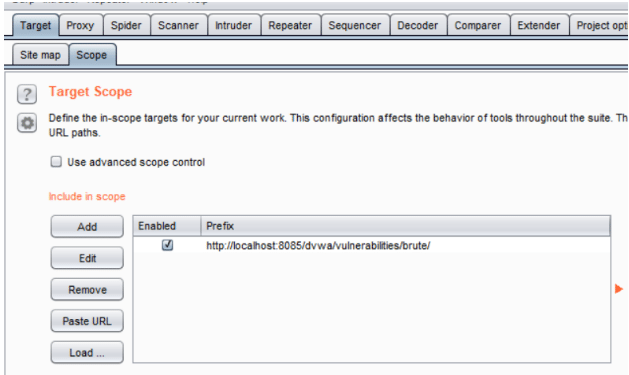
Navigate to Proxy>Intercept tab and make sure the Intercept button reads “Intercept is on”.
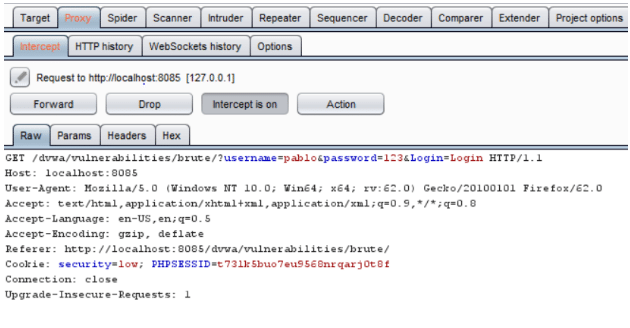
Now we’ll actually capture traffic moving on DVWA and try to implement a brute force attack on the vulnerable system. Change proxy to manual as explained at the start. Switch tab to DVWA and enter ‘pablo’ in the username field and ‘123’ in the password field(password field text is optional). Click on login, burp suite will capture the request of the login page. Various details of the web page will be visible to the Ethical Hacker, like in this case the session ID, username & password input fields are detectable.
Repeater
Repeater is a very useful tool which is used to manually manipulate any part of the HTTP request headers and one can gauge what the response looks like.
To send captured data to Repeater, select Actions tab or right-click in the window where captured parameters are displayed and select ‘Send to Repeater’.
Now go to the repeater tab and click on ‘Go’
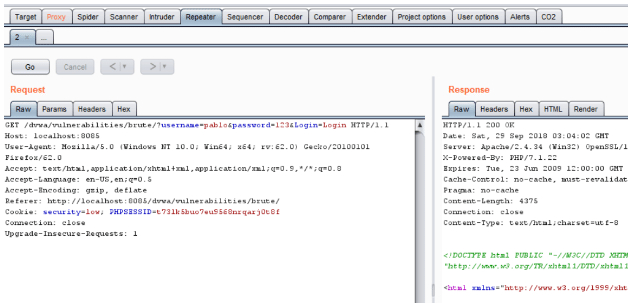
You can see the site interface response under ‘Render’ tab
Intruder
Intruder is used in automating customized attacks against web applications. We’ll set positions and payload according to the fields to be exploited and type of attack.
Go to Intruder>Positions and clear the selected parameters by clicking on ‘Clear’.In this example, we’re trying to find the value for a single parameter password so the attack type is Sniper. There are other attack types such as Battering ram,Pitchfork and, Cluster bomb. Select the password you submitted and click on ‘Add’
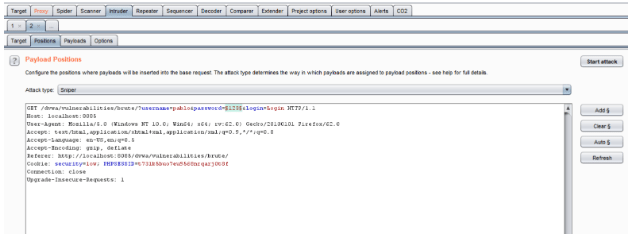
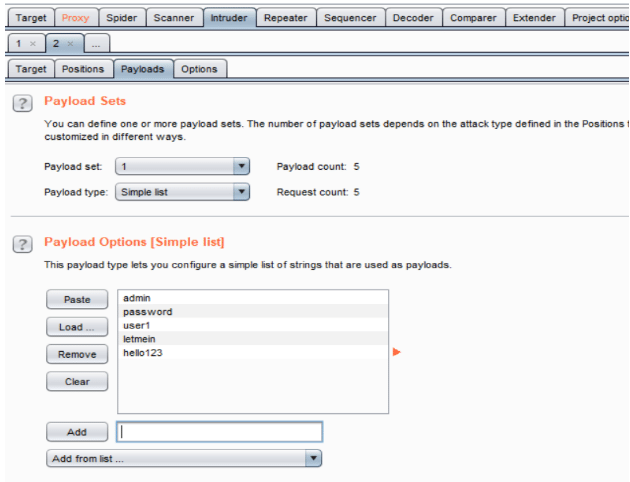
Next, Intercept>Payload to select a payload list from the available ones(can be found under ‘Add from list’) or use a customized dictionary list. Once the payload is set, click on start attack and sit back and let Burp do the job for you. The time required for Burp Suite to go through all values depends on the size of the list as well as the edition, the Pro edition is visibly faster than the Community(free) edition.
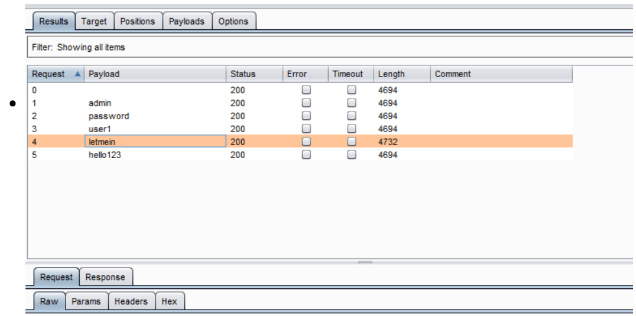
A new window pops up with the Intruder scan results. In this case, we can see ‘letmein’ stands out uniquely from the other inputs. Go to Repeater or browser and test this password.
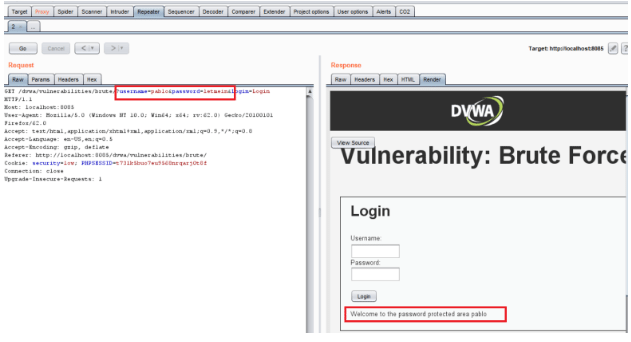
Voila!
A lot more can be done using these extensible tools that PortSwigger has provided us with but that is out of scope for a novice guide.
BurpSuite provides coverage of over 100 generic vulnerabilities, including the OWASP top 10. However, always validate the scan and test results as no automated tool is perfect.