The dark web is the hidden collective of internet sites only accessible by a specialized web browser. It is used for keeping internet activity anonymous and private, which can be helpful in both legal and illegal applications. While some use it to evade government censorship, it has also been known to be utilized for highly illegal activity.
However, the ‘surface web’ that we use every day is estimated to be less than a thousandth of the entire web! The rest is in the ‘deep web’: invisible content not indexed by search engines. It contains databases, password-protected websites, intranets, academic journals, and archives, some of it is accessible through specific applications or with credentials.
One portion of the deep web belongs to the ‘dark web’ – a space without a centralized structure and with non-indexed and volatile content accessible only with special browsers. Even though the dark web is often associated with being malicious, it is also used for a good purpose, the dark web enables the communication of human rights activists and whistle-blowers around the world.
The dark web also hosts markets of illegal goods such as counterfeit products, drugs, and financial crime services such as money laundering and bank frauds. There is an ugly side to it as well: markets offering pedophilia content, hitman services, conventional and chemical weapons purchase, and illegal medical research. It is also used for cyber contraband, the process of transferring illegal items through the internet (such as encryption technology, child pornography) that is barred in some locations.
Breaking down the construction of the dark web reveals a few key layers that make it an anonymous haven:
- No webpage indexing by surface web search engines. Google and other popular search tools cannot discover or display results for pages within the dark web.
- “Virtual traffic tunnels” via a randomized network infrastructure.
- Inaccessible by traditional browsers due to its unique registry operator. Also, it’s further hidden by various network security measures like firewalls and encryption.
Accessing the Dark Web

The dark web can be accessed by TOR(The Onion Router) Browser. Think of Tor as a web browser like Google Chrome or Firefox. Notably, instead of taking the most direct route between your computer and the deep parts of the web, the Tor browser uses a random path of encrypted servers known as “nodes.” This allows users to connect to the deep web without fear of their actions being tracked or their browser history being exposed. The client request is routed through a large number of other clients and thus the ending address can never be determined thus maintaining anonymity.
Sites on the deep web also use Tor (or similar software such as I2P, the “Invisible Internet Project”) to remain anonymous, meaning you won’t be able to find out who’s running them or where they’re being hosted.
Threats on Dark Web
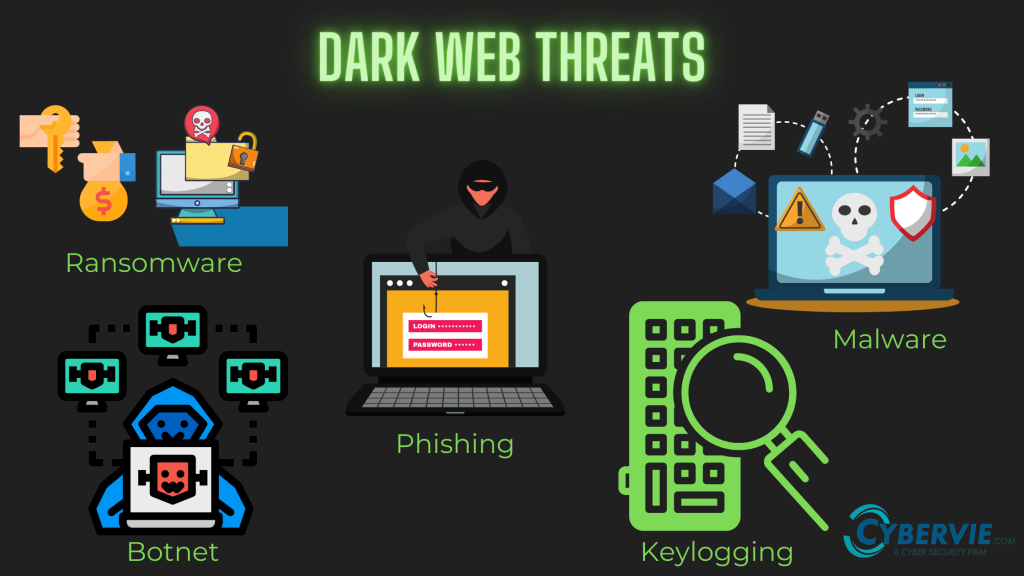
- Malicious software– The dark web is a hub of malware and if proper care is not taken, the results may be devastating. users can find themselves regularly exposed to some types of malware like:
- Keyloggers
- Botnet malware
- Ransomware
- Phishing malware
- Government Monitoring– With many Tor-based sites being overtaken by police authorities across the globe, there is a clear danger of becoming government target for simply visiting a dark website. By utilizing custom software to infiltrate and analyze activity, this has allowed law officials to discover user identities of patrons and bystanders alike. Even if you never make a purchase, you could be watched and incriminate yourself for other activities later in life.
- Scams– Some alleged services like the professional “hitmen” may just be scams designed to profit from willing customers. Reports have suggested the dark web offers many illegal services, from paid assassinations to trafficking for sex and weapons.
Ways one can safely browse through the Dark Web:
- Trust your intuition. To avoid being scammed, you’ll want to protect yourself with smart behaviour on the web. You should always take action to remove yourself from a situation if something doesn’t feel right.
- Detach your online persona from real life. Your username, email address, “real name,” password, and even your credit card should never be used anywhere else in your life. Create brand-new throwaway accounts and identifiers for yourself if necessary. Acquire prepaid, unidentifiable debit cards before making any purchases. Do not use anything that could be used to identify you — whether online or in real life.
- Employ active monitoring of identify and financial theft. Many online security services now offer identity protection for your safety. Be sure to take advantage of these tools if they are made available to you.
- Explicitly avoid dark web file downloads. Fear of malware infection is significantly higher in the lawless territory that is the dark web. Real-time file scanning from an antivirus program can help you check any incoming files in case you do opt to download.
- Use a secondary non-admin local user account for all daily activities. The native account on most computers will have full administrative permissions by default. Most malware must take advantage of this to execute its functions. As such, you can slow or halt the progress of exploitation by limiting the account in-use to strict privileges.
- Always restrict access to your Tor-enabled device. Protect your children or other family members so they aren’t at risk of stumbling across something no one should ever see. Visit the Deep Web if you’re interested, but don’t let kids anywhere near it.
For more blogs like this please go to our Blog Page








