Introduction
Explanation of what DNS Sinkholes is?
One cybersecurity technique called DNS Sinkholes is used to redirect malicious traffic to a non-existent or controlled server. This technique involves responding to a device’s DNS query with an incorrect or non-existent IP address causing it to connect to a dead end or controlled server. DNS Sinkhole can prevent malware or other malicious traffic from reaching its intended target and block access to specific websites by redirecting their domain names. It is an effective way to enhance network security and prevent known malicious traffic.
Brief explanation of how it works?
When a device tries to connect to a website or server, it first sends a request to the DNS server to obtain the IP address associated with the domain name. In a DNS Sinkhole, the DNS server responds to the request with an incorrect or non-existent IP address. This response causes the device to connect to a dead end or a controlled server instead of the intended destination. The controlled server can be used to monitor and analyze malicious traffic or to redirect the traffic to a harmless destination. The DNS Sinkholes technique effectively blocks the device from connecting to the intended malicious server or website preventing malware or other malicious traffic from causing harm to the network.
How DNS Sinkhole Works?
Overview of how DNS servers function
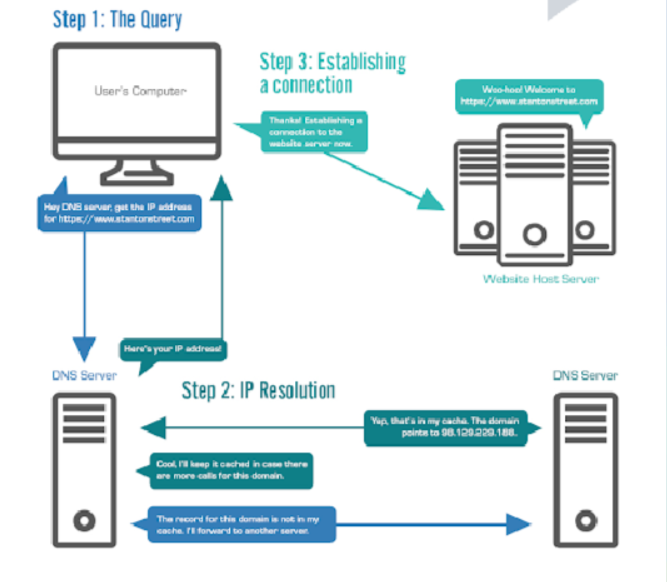
DNS servers play a critical role in the functioning of the internet by translating human-readable domain names into machine-readable IP addresses. When a user types a domain name into their web browser, the browser sends a request to the DNS server to obtain the IP address associated with that domain name. The DNS server then responds with the corresponding IP address allowing the user’s device to connect to the website or server.
Explanation of how DNS sinkholes redirects malicious traffic
DNS Sinkhole is a method that is employed to redirect malicious traffic towards a non-existent or controlled server. To achieve this, the DNS server keeps a list of malicious domain names or IP addresses that are known as a blacklist. Whenever a device requests the DNS server for a domain name that is present in the blacklist the DNS server responds with an incorrect or non-existent IP address. This response causes the device to connect to a dead end or controlled server rather than the intended destination. The controlled server can be utilized to analyze and monitor malicious traffic or to redirect the traffic towards a harmless destination.
Technical details on how DNS sinkhole works
One way to implement DNS Sinkholes is through the use of DNSmasq, an open-source tool that serves as a lightweight DNS server to redirect malicious traffic to a controlled server. To set up DNSmasq as a DNS sinkhole, the administrator needs to create a blacklist of known malicious domain names or IP addresses and configure DNSmasq to respond to DNS queries for these domains with an incorrect or non-existent IP address. This response then diverts the device to a dead end or a controlled server blocking it from reaching its intended destination.
Apart from DNSmasq, there are other open source tools such as Pi-hole,BIND etc used to configure DNS sinkhole.
DNS Sinkholes can also be implemented on enterprise-grade firewalls or intrusion detection systems, which can provide more advanced capabilities such as real-time blacklists and automatic updates. These systems can be configured to automatically block traffic from known malicious sources and redirect it to a controlled server for analysis. DNS Sinkhole is an effective way to improve network security by blocking known malicious traffic and preventing it from causing harm to the network.
Benefits of DNS Sinkholes for Network Security
Explanation of how DNS sinkhole blocks malicious traffic
DNS Sinkholes blocks malicious traffic by intercepting DNS requests for known malicious domain names or IP addresses and redirecting them to a non-existent or controlled server. By doing so DNS Sinkhole prevents devices from connecting to known malicious sites and downloading or transmitting malware, spyware or other malicious content. DNS Sinkhole can also be used to block communication with command-and-control servers used by botnets, which can prevent infected devices from receiving instructions to carry out attacks.
Discussion on how DNS Sinkhole can be used to block access to specific websites
DNS Sinkholes can not only block known malicious sites but also restrict access to specific websites that are considered inappropriate or undesirable in a network environment. Companies or schools may utilize DNS Sinkhole to block social media sites to enhance employee productivity or prevent students from accessing adult content. With DNS Sinkhole blocking access at the DNS level it can serve as an efficient means to enforce web content filtering policies.
Examples of how DNS Sinkholes can be used in the real world
One way DNS Sinkhole has been applied in real-world situations is to enhance network security. In 2012, for instance, the FBI employed DNS Sinkhole to dismantle the GameOver Zeus botnet, which was accountable for stealing millions of dollars from banks and other institutions. By redirecting traffic from compromised devices to a managed server, the FBI was able to gather intel about the botnet’s infrastructure and shut down the command-and-control servers.
DNS Sinkholes has also been used by security researchers to analyze the behavior of malware and other types of malicious traffic. By redirecting traffic to a controlled server, researchers can observe how the malware behaves and gather information about its capabilities and communication protocols.
Trends in DNS Sinkholes
- Machine Learning and AI : As the number and complexity of cyber threats continue to increase, machine learning and artificial intelligence are becoming increasingly important tools for improving network security. DNS Sinkhole technology can be enhanced with machine learning algorithms that can identify and block new and emerging threats based on their behavior and other characteristics. By constantly learning and adapting, these systems can stay ahead of cybercriminals and provide more effective protection against a wide range of threats.
- Integration with Cloud Services : As more organizations move their applications and infrastructure to the cloud, DNS Sinkhole technology is likely to become more integrated with cloud-based services. This could include cloud-based DNS servers that can provide more robust and scalable protection against cyber threats as well as cloud-based threat intelligence services that can provide real-time updates on new and emerging threats.
- Blockchain-Based DNS : Blockchain technology has the potential to revolutionize the way DNS servers function by providing a decentralized and more secure method for translating domain names into IP addresses. Blockchain-based DNS servers can provide more robust protection against DNS-based attacks and could be integrated with DNS Sinkholes technology to provide even more effective protection against cyber threats.