Today we are going to see about what is vulnerability in web application security.
What is Vulnerability?
A vulnerability is a security hole in software or an operating system that provides a potential way or angle to attack the system.
Basically, vulnerability is a weakness or flaw in a system.
and a vulnerability can be as small as weak passwords and as complex as buffer overflow.
Impact of Vulnerability

A Vulnerability has a very heavy impact on the software or website, as it can be exploited for bad purposes.
If there is a vulnerability in your system and you don’t know about it, someone may be exploiting it and gaining all the important and crucial information.
For example
There is a SQL injection flaw on your website and you do not know about it.
The hackers can exploit this vulnerability to gain all the information stored in your database just by entering some codes, and you will end up giving all of your website information and your database is leaked because of this flaw.
So you can see how big impact a vulnerability can cause in your system.
Vulnerability is the intersection of three elements
- A system susceptibility or flaw.
- Attackers access to the flaw.
- Attackers capability to exploit the flaw.
What are the Causes of vulnerbility?
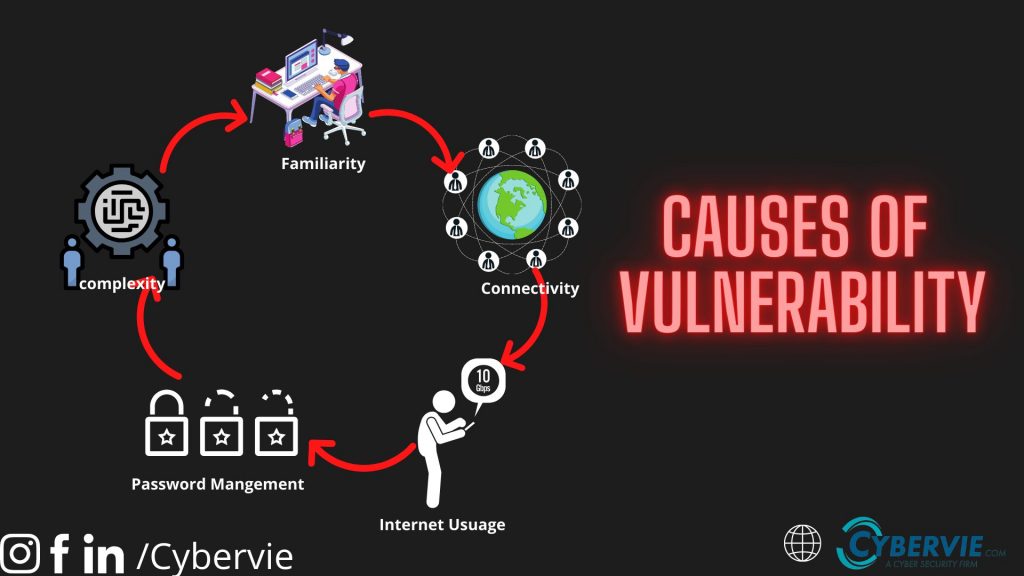
There can be many causes of vulnerability because it changes with technology.
some causes are,
- Complexity: Large and complex system has the highest probability of vulnerability because of unintended access points
- Familiarity: Using well-known software or codes can increase the probability in the system because hackers are familiar with these well-known tools and how to exploit them.
- Connectivity: Connectivity increase the chance of vulnerability. As more device is connected to the network more are the chances of flaw.
- Password management: Weak passwords can let hackers brute-force your password and gain access.
- Internet usage: The Internet is full of spyware and adware which can be installed automatically on the computer.
And there are lots of causes which can result in vulnerable system.
Tools for finding a vulnerability
There are some tools we can use for full vulnerability analysis.
- Nikto2: Nikto is an Open Source web server scanner that performs comprehensive tests against web servers for multiple items, including over 6700 potentially dangerous files/programs, checks for outdated versions of over 1250 servers, and version specific problems on over 270 servers
- Netsparker: It is another web application vulnerability tool with an automation feature available to find vulnerabilities. Can find thousands of vulnerabilities within hours.
- OpenVAS: OpenVAS is a full-featured vulnerability scanner. Its capabilities include unauthenticated testing, authenticated testing, various high-level and low-level Internet and industrial protocols, performance tuning for large-scale scans, and a powerful internal programming language to implement any type of vulnerability test.
- W3AF: w3af is a Web Application Attack and Audit Framework. The project’s goal is to create a framework to help you secure your web applications by finding and exploiting all web application vulnerabilities.
And there are lots of tools, the list will goes on if we mention all of them.
How to avoid common web security vulnerbility
1. Don’t Use Random codes

Do not use random codes from strangers and copy-paste them on the website.
Never copy-paste codes from GitHub or any other website and use them on your website. Research about the code, And read the code thoroughly and check if there is nothing fishy.
Who knows if there is some malicious code in that pile of code and you end up compromising your system. Hacker can pawn systems with just 2 or 3 lines of code, so beware.
2.Encrypt the sensitive information
Encrypt all of the sensitive data which can be seen in code as plain-text.
Always use a good and reliable algorithm or encryption to encrypt you sensitive data like AES 256 which is one of the best encryption verified by NSA.
3.Patch it immediately
As soon as you find out about the vulnerability work on its patch, because there are some vulnerabilities that you can’t detect previously like Zero-Day exploits.
So, as soon as it is exposed patch it immediately so that it can’t be exploited further and cause harm to the system.
4. Be Aware
Always be aware of the latest vulnerability because it also develops with technology. Keep an eye on the latest vulnerabilities and check for them on your system.








