Evading AV with simple malwares
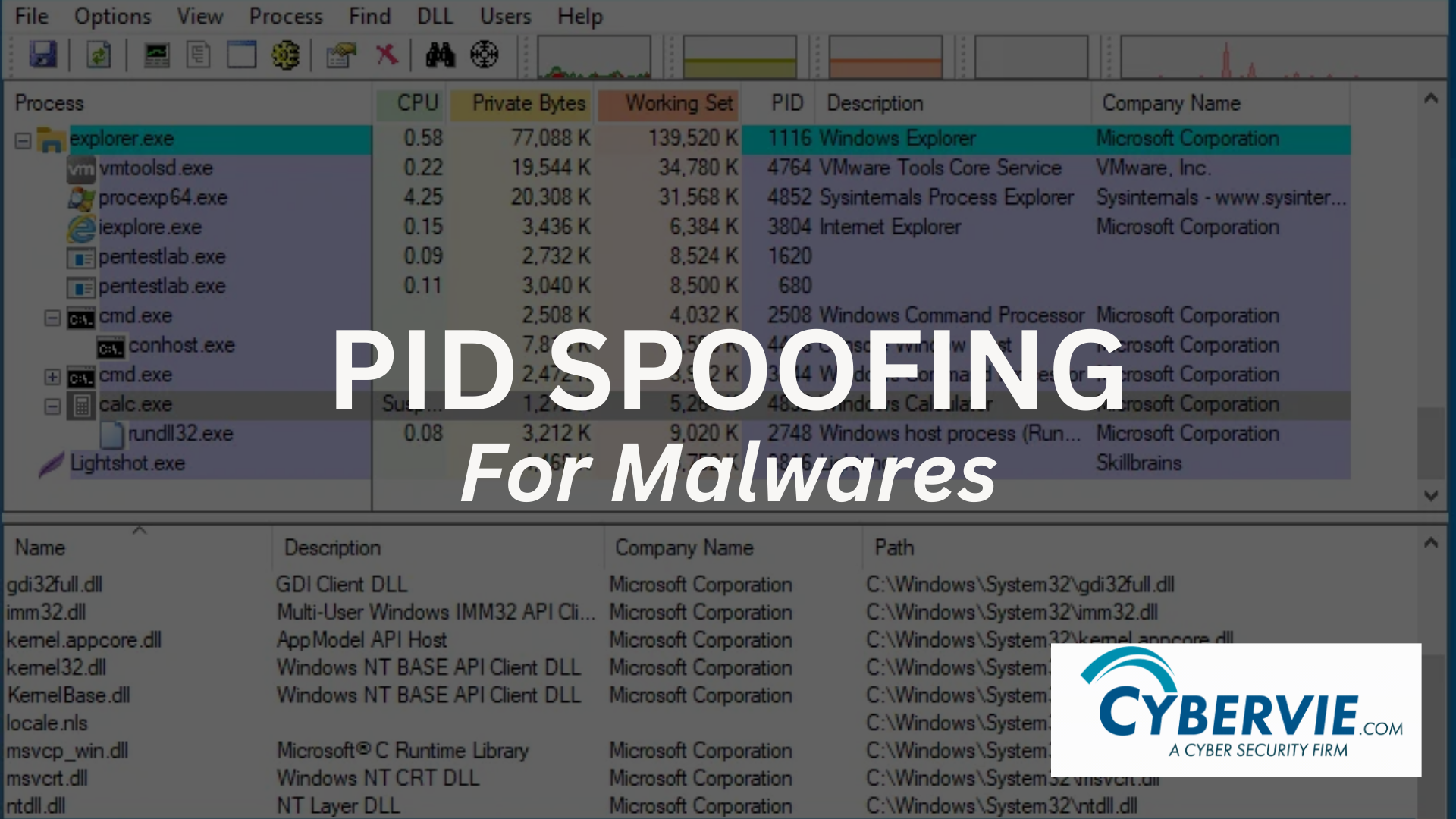
Evasion is a cat and mouse game in the cybersecurity field. Lets dive deep into it and see some simple tricks for deception. Process ID (PID) spoofing is a sneaky technique used by malware to trick computer systems. Every program running on a computer is given a unique identification number called a Process ID, or PID for short. This PID helps the system monitoring each […]
DNS Sinkholes: How Redirecting Malicious Traffic Can Improve Network Security?

Introduction Explanation of what DNS Sinkholes is? One cybersecurity technique called DNS Sinkholes is used to redirect malicious traffic to a non-existent or controlled server. This technique involves responding to a device’s DNS query with an incorrect or non-existent IP address causing it to connect to a dead end or controlled server. DNS Sinkhole can […]
Incident Response as a Service and its importance in Cyber Security.

What is Incident Management & Response as a Service? Incident Response as a service is a methodical technique to detecting, mitigating, and managing potential cyberattacks. The primary goal of the incident response process is to assist companies in minimizing the unwanted threats caused by a breach, recovering as swiftly as possible, and actively planning for […]
Analyzing OneNote Malware: A Technical Investigation

OneNote and its Purpose OneNote is a software developed by Microsoft that facilitates digital note-taking, enabling users to capture, store and share information across different devices. The application serves as a repository for managing notes, research, ideas and other types of content. Its features include handwriting and text recognition, audio and video recording, tagging, search […]
Breaking the Chain: Understanding and Preventing Supply Chain Attacks.

Definition and explanation of supply chain attacks and its examples A software supply chain attack is a type of cyber attack that targets an organization’s supply chain by exploiting vulnerabilities in a third-party supplier or vendor’s systems. Supply chain attack example means attack can lead to the theft of data, installation of malware, or control […]
Why Mobile Device Security? Empowering you to stay safe and secure.
Introduction to Mobile Device Security Mobile devices have become a must have in our daily lives, and we use them for various purposes such as communication, entertainment, shopping, banking, geo-location etc. With the increasing use of mobile devices in our day to day lives , the need for mobile device security has also become more […]


