Juice Jacking – A Concise Overview

What is Juice Jacking? Juice jacking is a type of cyber attack where you unknowingly plug in your mobile or electronic device into a USB port that is infected with malware which then gets loaded on the phone once a connection is made. This malware can violate your privacy by gaining direct access to […]
Cyber Weekly 42-2022

This week’s latest Cybersecurity updates Bolster Raises $15 Million to Tackle Fakes and Frauds. Keystone Health Data Breach Impacts 235,000 Patients. WordPress Security Update 6.0.3 Patches 16 Vulnerabilities. Google’s GUAC Open-Source Tool Centralizes Software Security Metadata. FBI Warns of Iranian Cyber Firm’s Hack-and-Leak Operations. Critical Flaw Reported in Move Virtual Machine Powering the Aptos Blockchain […]
What is Kerberosting

What is Kerberoasting ? The general concept of Kerberoasting is requesting service tickets (TGS) from the KDC (Kerberos Domain Controller) that are associated with service accounts to retrieve their hashes. Then, attempt to crack them offline with tools like Hashcat or John to recover the cleartext passwords to either escalate privileges vertically to become a local administrator or horizontally to access a set of different resources that can […]
How to find hidden directories in a website

The reconnaissance and scanning phases of a penetration test are arguably the most important of the entire process. Without a clear understanding of the bigger picture and the avenues potentially available to you, you won’t be going very far at all. As part of this process, it’s very likely that you regularly come up against […]
How to use Proxychains
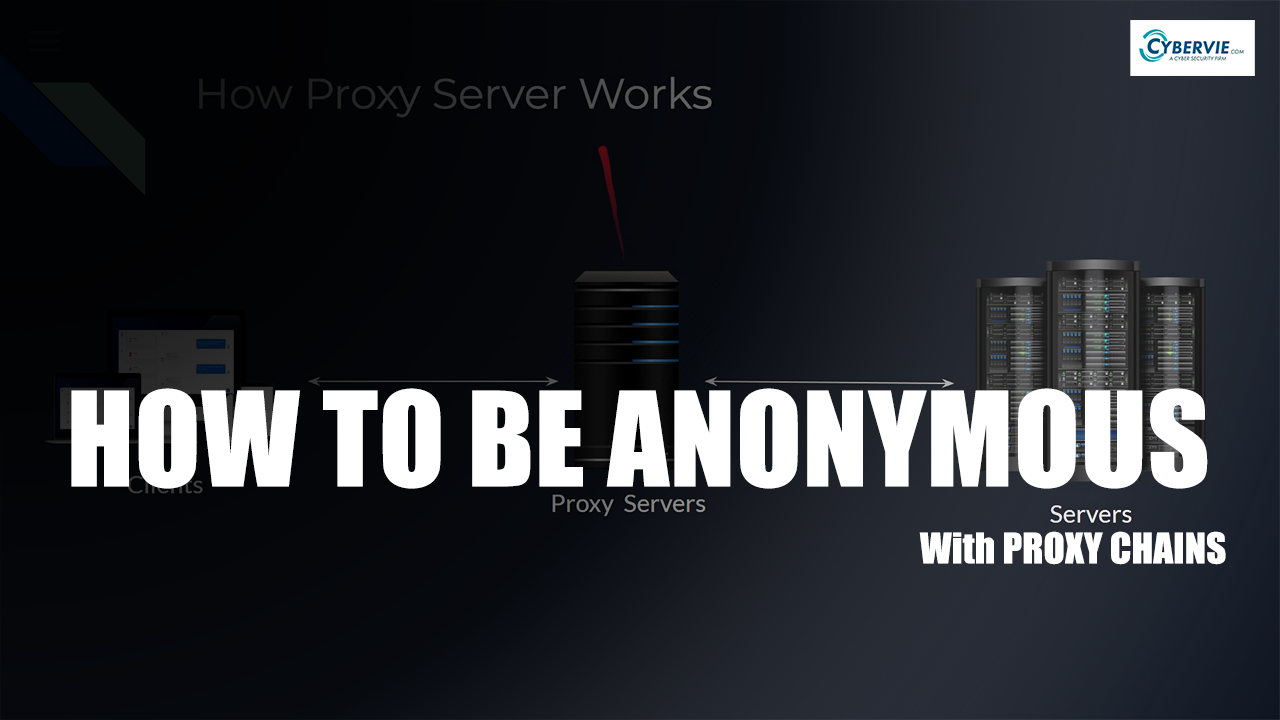
Using a Linux-based operating system to hide your identity on the internet is quite simple, and you can do it all without paying for a VPN service like those available today. Kali Linux distributions are used to test the security of WiFi networks, websites, and servers, among other things. Operating systems like Debian and Ubuntu are also […]
Data privacy vs Data security
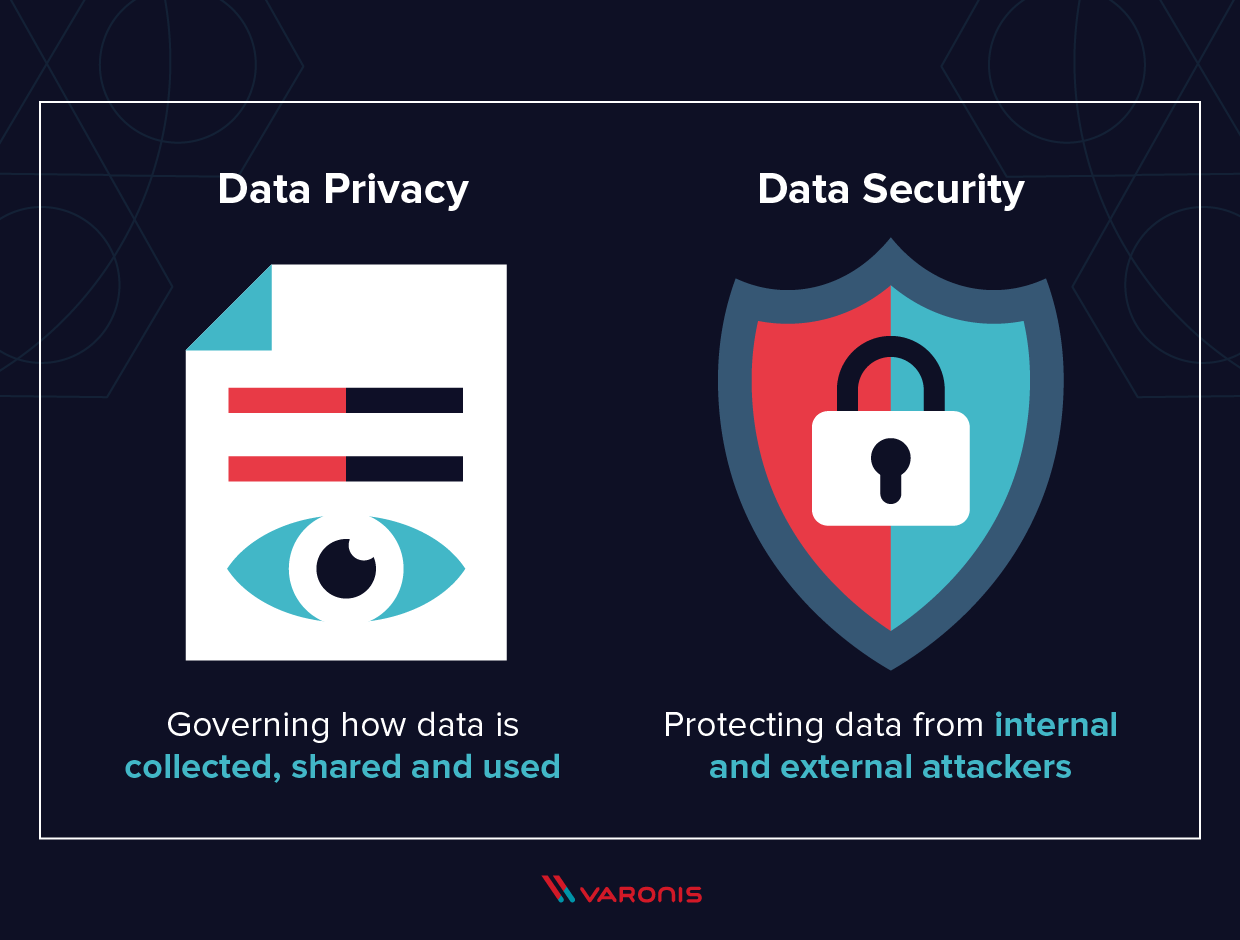
When it comes to data security and data privacy, these terms are often exchanged. Whether these are synonyms , closely connected with each other or do have some difference? Let’s clear this through this post. Firms who manage and collect their data needs protection and security in a well manner. So what is privacy and […]


