What is Kerberosting

What is Kerberoasting ? The general concept of Kerberoasting is requesting service tickets (TGS) from the KDC (Kerberos Domain Controller) that are associated with service accounts to retrieve their hashes. Then, attempt to crack them offline with tools like Hashcat or John to recover the cleartext passwords to either escalate privileges vertically to become a local administrator or horizontally to access a set of different resources that can […]
Cybersecurity Interview Questions Part-3

In the continuation of our interview questions series, here we present the next part of our interview questions, Lets begin: Q1. Name some malware identification tools. Some of the mostly used tools in identification of malware is: CrowdStrike Falcon Insight EDITOR’S CHOICE This EDR analyzes malware on two levels and also identifies intruder activity. The […]
Linux File System
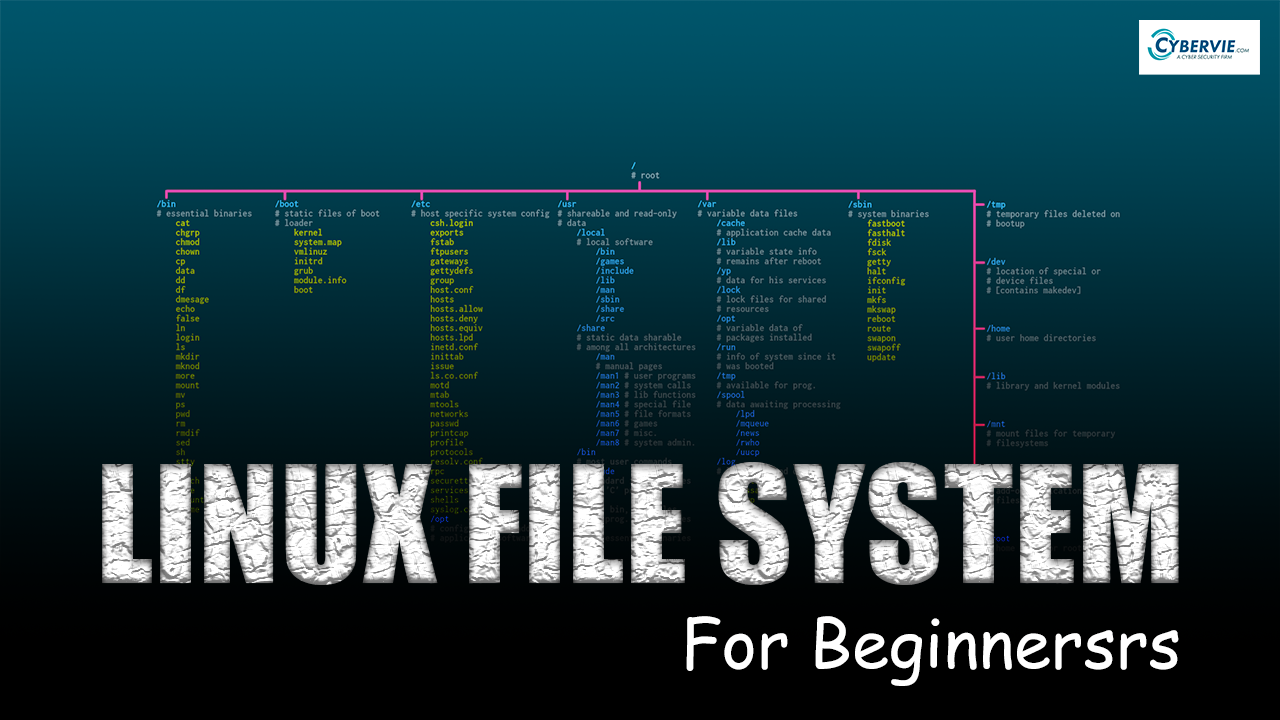
Linux File System If you are in IT Field or thinking of getting into it. Then a deep understanding of Linux is very important. In this article, we are going to get a decent understanding of Linux File System. What is a File System ? OS stores data on disk drives using a structure called […]
Information security: A parent tier Vs Ethical hacking

Introduction- Today in this world, we uses variety of information. Therefore, experts established different areas to secure these information. Such areas are Information security, Cybersecurity, and Ethical hacking. In our previous post we learnt about difference between three closely related terms I. e Cyber security, network security and information security. But do you all know what […]
Cyber Threat Intelligence | Beginners Guide

In this article we are going to learn about threat intelligence domain.
Pureblood | Penetration Testing Framework

In this article, we are going to learn about a tool called Pureblood created by ChesZy2810. Pureblood is a Web Penetration Testing Framework written in Python. About Pureblood can perform Web Application Penetration testing And Web Application attacks. Web Application Penetration Testing includes. Web Pentest / Information Gathering: Banner Grab Whois Traceroute DNS Record Reverse […]


