How to use Proxychains
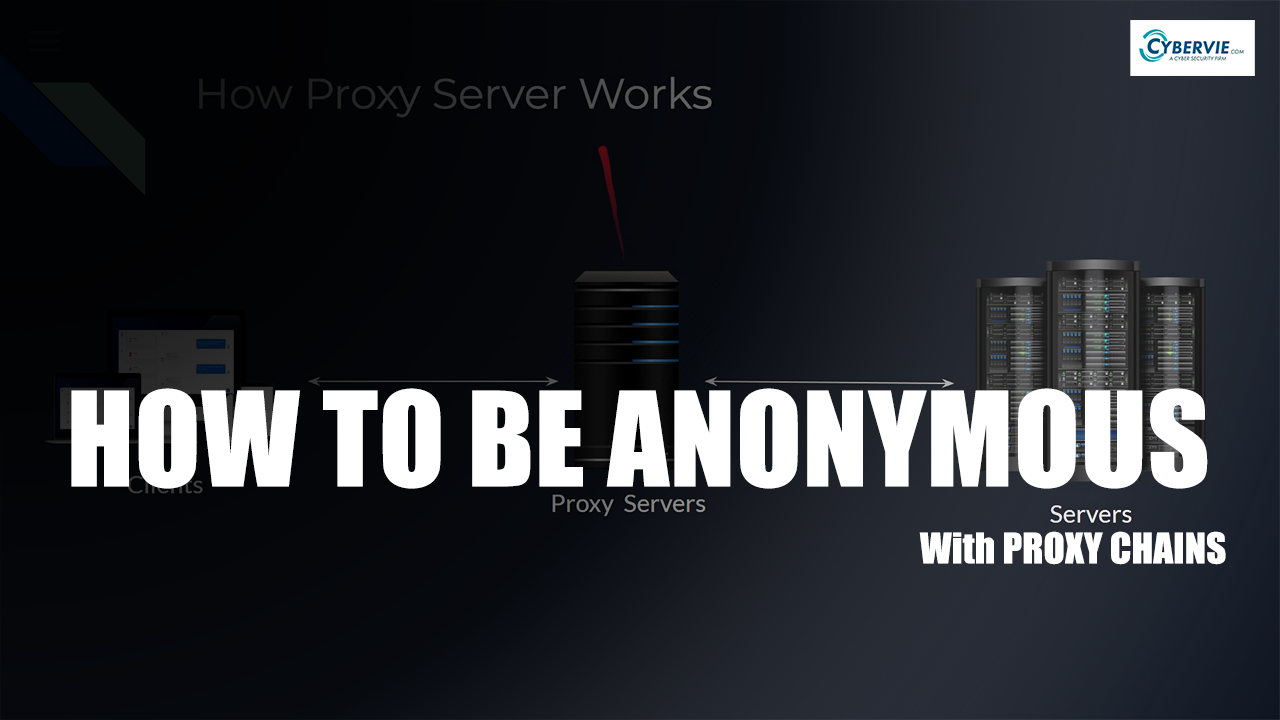
Using a Linux-based operating system to hide your identity on the internet is quite simple, and you can do it all without paying for a VPN service like those available today. Kali Linux distributions are used to test the security of WiFi networks, websites, and servers, among other things. Operating systems like Debian and Ubuntu are also […]
Linux File System
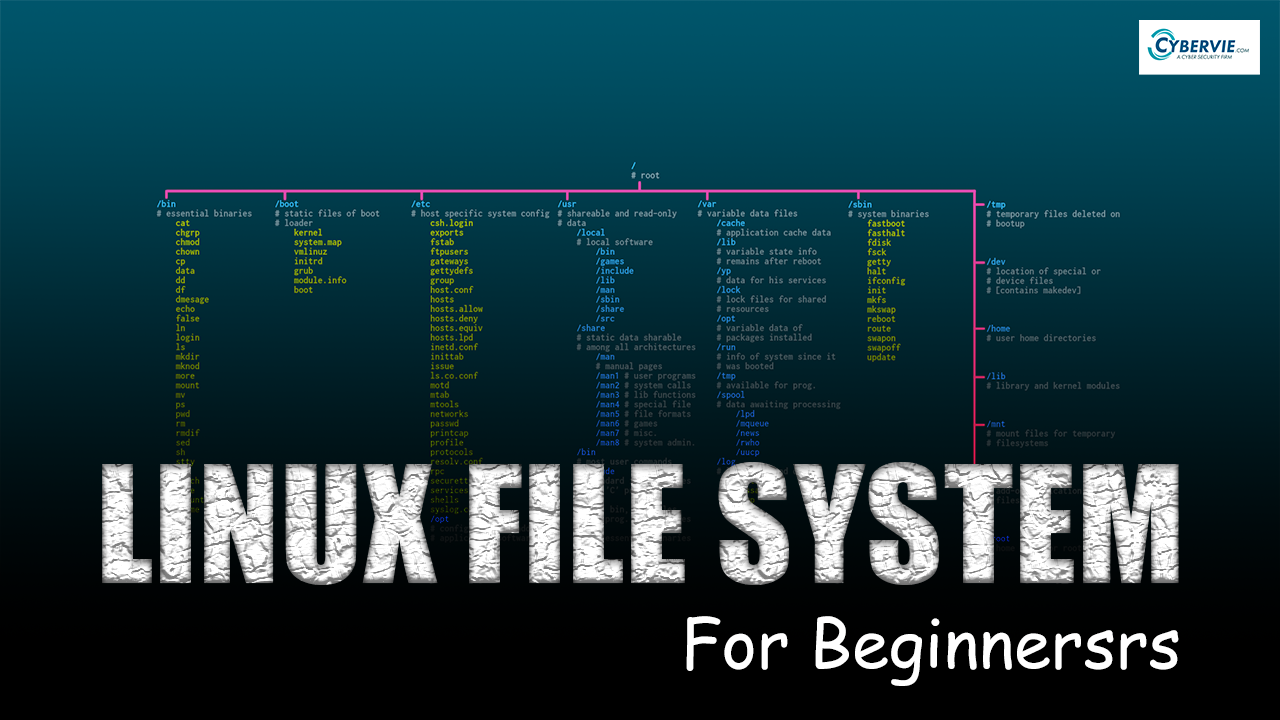
Linux File System If you are in IT Field or thinking of getting into it. Then a deep understanding of Linux is very important. In this article, we are going to get a decent understanding of Linux File System. What is a File System ? OS stores data on disk drives using a structure called […]
Kali Linux 2021.2 | Everything You Have to Know

In this article we are going to discuss about Kali Linux 2021.2 release
What is Maltego? | How to use it for Information Gathering.

In this article we are going to learn about a software name Maltego which is used for Information gathering and OSINT research
Phishing Attack – Step by step Demo using Kali Linux Free Tool!
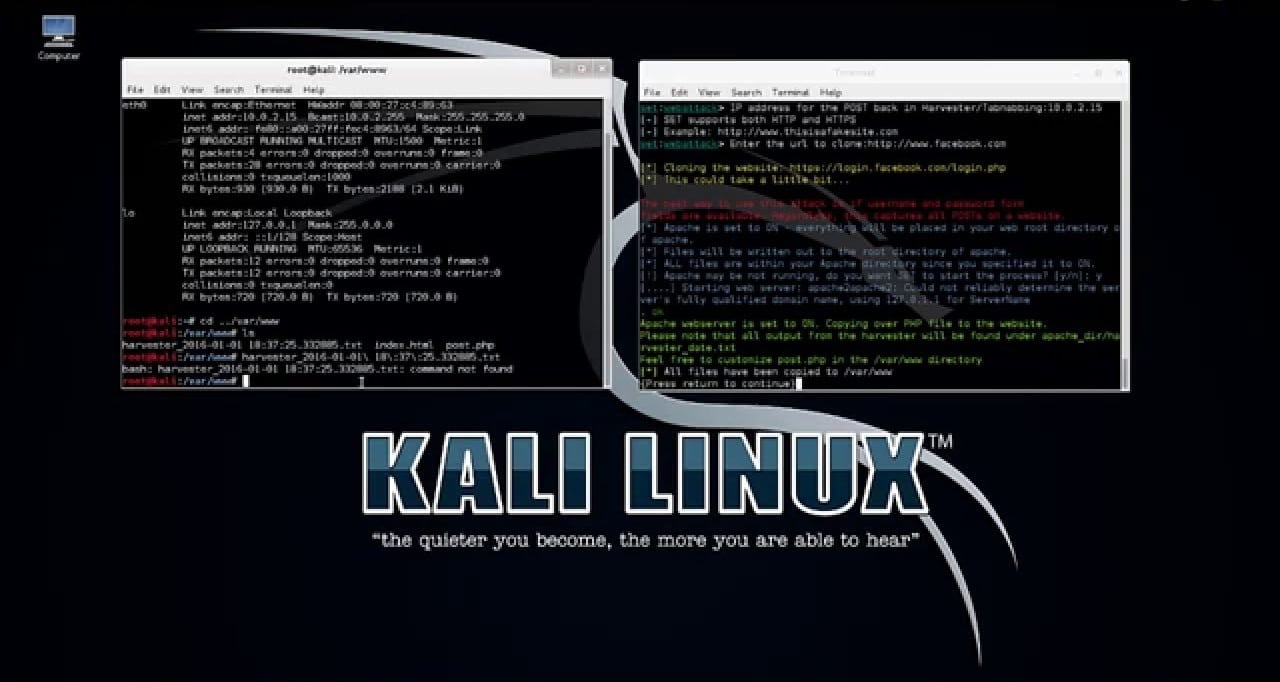
Phishing is a form of cyber attack which typically relies on email or other electronic communication methods such as text messages and phone calls.


