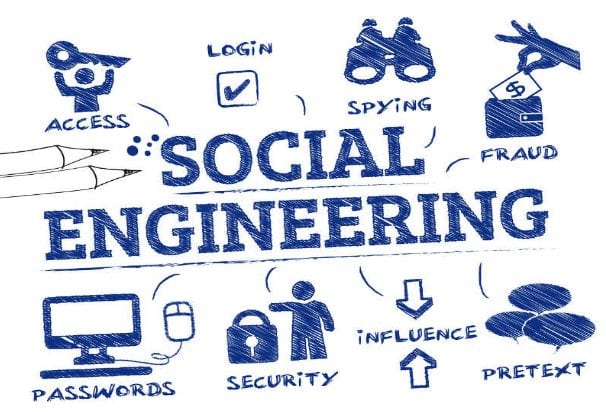
Social Engineering attacks involve manipulating human psychology using various resources like phone calls and social media to trick the employees of certain organizations or individual users into revealing confidential or sensitive information. This attack type tends to go unnoticed by the general populace as there is not enough awareness. As a result, hackers use various methods of infiltration. Thus a legitimate solution to the problem such as investing in new technology is imminent. In this article, we will explore the life cycle of social engineering attacks and briefly describe the attack techniques and state safety measures against these attacks.
It is a popular hacking technique as it is relatively easy to exploit human kindness, urgency, curiosity among other emotions. Also, it relies on the errors of legitimate human users. Thus making it difficult to identify and prevent such an attack. People can be influenced easily to gain unauthorized access to a system or to disperse malware by following certain steps:
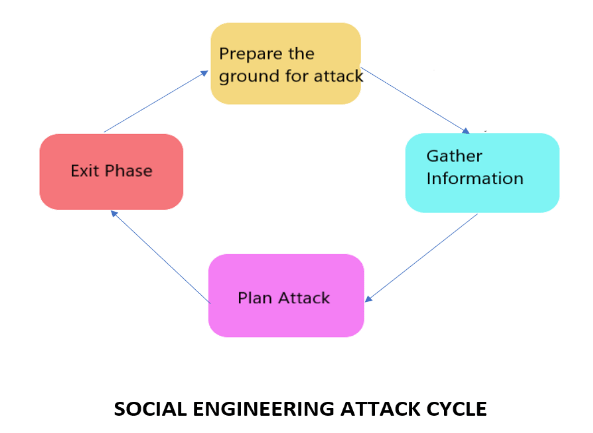
- Prepare the ground for an attack: Attackers performs research on the intended target by tracking behaviours and patterns of the individual they’re after. If it is a company, they will first find out the internal operations and employee structure, accordingly, choose a target human and find out about them by going through their social media.
- Gather information: This is the engaging phase. Once there is sufficient background information on a user, the attacker conceals their identity and poses as a trusted individual in order to get the required data.
- Plan attack: Based on the reconnaissance phase, the hacker will design an attack including computer programs and tools to use which will be most effective and will leave a minimum trail.
- Exit phase: Once a vulnerability is successfully exploited, social engineers need to cover their tracks to avoid any suspicions. They delete any trace of malicious code and try to bring things to a natural end.
Popular techniques that social engineers commonly use to target their victims:
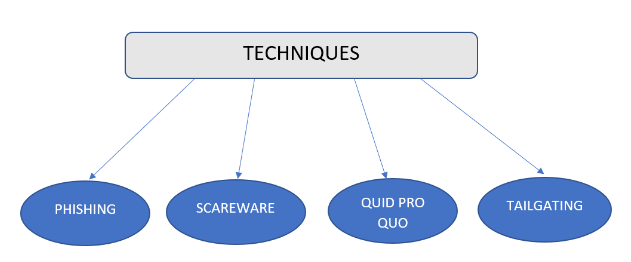
Phishing: As one of the most popular types of social engineering, phishing uses emails and text messages disguised as a licit organisation. Attackers try to trick users into opening malicious links or opening files. These contain malware and create a sense of urgency or fear in a naive computer user.
Scareware: Also referred to as deception software, target users are tricked into thinking that their device is affected by malware. They are bombarded with bogus threats and alerts about the safety of their device. This prompts them to install certain software which has no real benefit or is malware itself.
Quid pro quo: Here, an attacker promises certain benefits in exchange for user information or assistance. They may pose as IT service people and pretend to provide quality service to their systems while actually doing the opposite. This social engineering method is very similar to baiting. The only difference being that baiting promises goods while quid pro quo provides services.
Tailgating: Often called piggybacking, tailgating relies on the courtesy of a person who has access to the company entrance. Hacker gains entry to a restricted area by waiting outside the building and following an authorised employee when they get the chance.
Preventing Social Engineering Attacks:
- Don’t open emails and attachments from questionable sources
- Don’t believe tempting offers
- Only use secure email and web gateways
- Use multifactor authentication
- Use updated antivirus software
Organisations must do their part in safeguarding themselves and thwarting social engineering attacks. They must identify which employees are prone to this attack and provide them security awareness training.
Social Engineers employ various methods to fool naive users. However, in hindsight, creating awareness about digital social engineering is necessary. This will create alert individuals who can protect themselves against most of these cyber attacks occurring in this day and age.