DLL Proxying
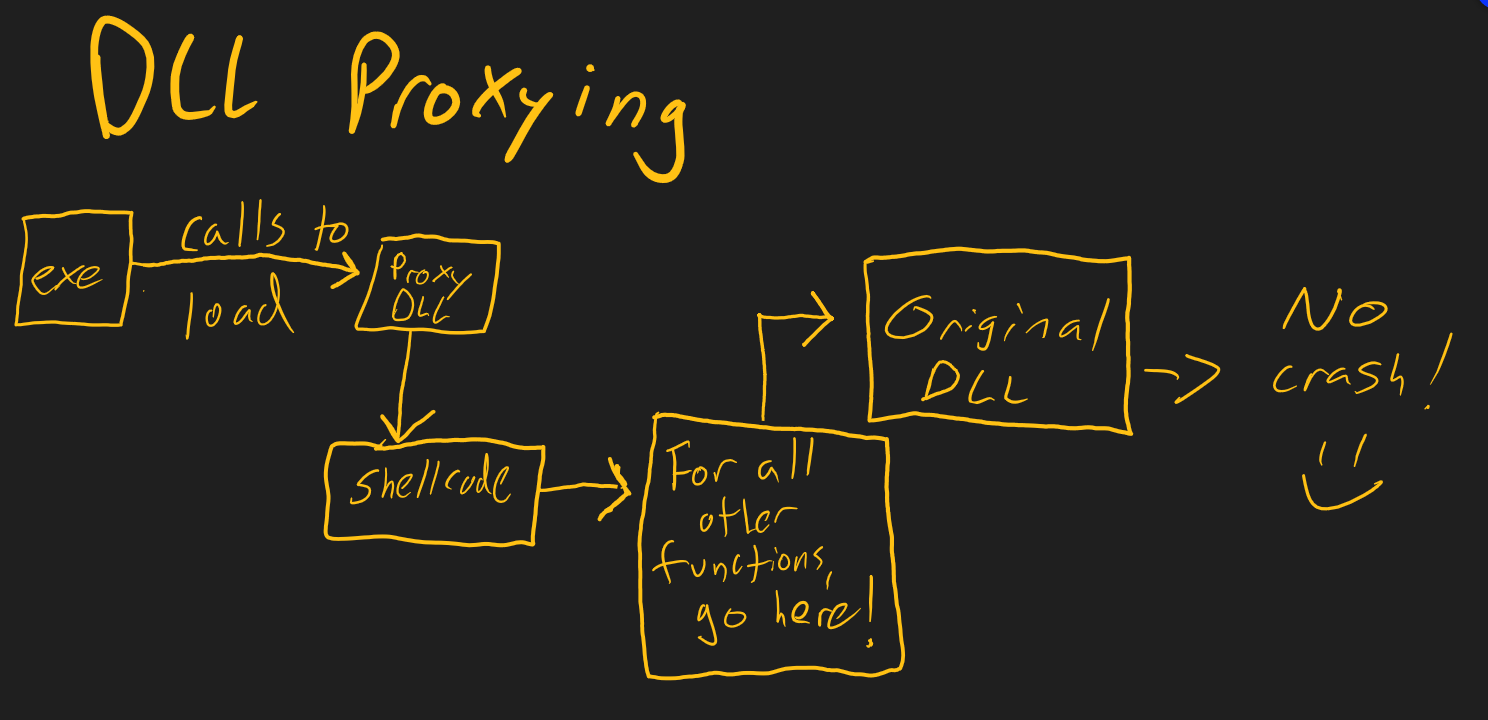
DLL Proxying : An SOC Nightmare DLL Hijacking, a cunning technique in the attacker’s arsenal, thrives on manipulating a program’s trust in external code. By strategically replacing legitimate DLLs (Dynamic Link Libraries) with malicious ones, attackers can gain unauthorized access, steal sensitive data, or wreak havoc on a system. To protect you organization as SOC […]
Evading AV with simple malwares
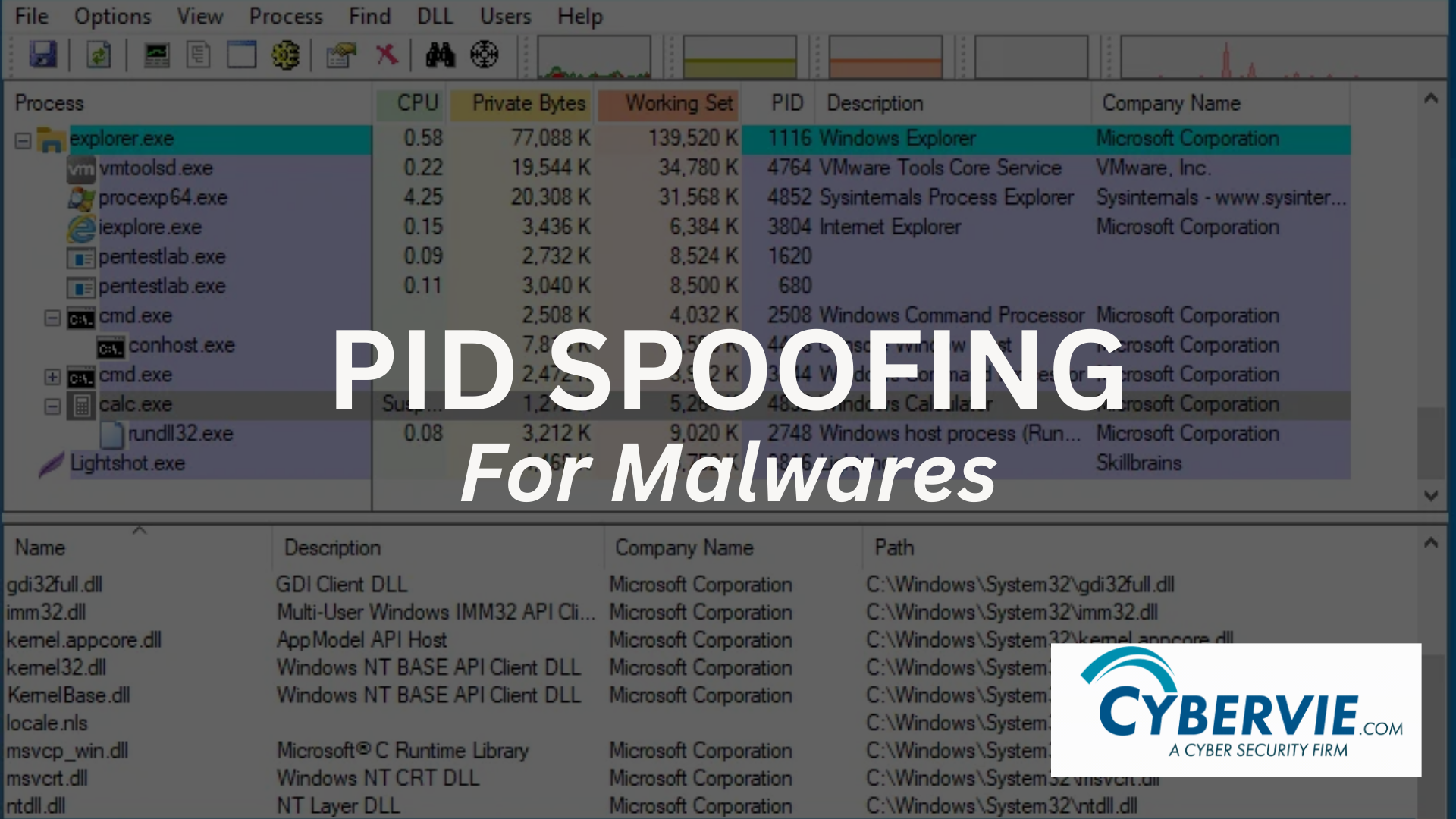
Evasion is a cat and mouse game in the cybersecurity field. Lets dive deep into it and see some simple tricks for deception. Process ID (PID) spoofing is a sneaky technique used by malware to trick computer systems. Every program running on a computer is given a unique identification number called a Process ID, or PID for short. This PID helps the system monitoring each […]


