In this article, we are going to learn about a tool name volatility. We will see what is volatility? How to install Volatility? and some basic commands to use and analyze memory dumps.
What is Volatility?
“Volatility is an open-source memory forensics framework for incident response and malware analysis. It is written in Python and supports Microsoft Windows, Mac OS X, and Linux” -Wikipedia
The Framework is a completely open collection of tools, implemented in Python under the GNU General Public License, for the extraction of digital artifacts from volatile memory (RAM) samples. The extraction techniques are performed completely independent of the system being investigated but offer unprecedented visibility into the runtime state of the system. The framework is intended to introduce people to the techniques and complexities associated with extracting digital artifacts from volatile memory samples and provide a platform for further work into this exciting area of research.
Basically, it helps us to analyze the volatile memory dumps and we can do lots of interactive things with the dump like –
- List all processes that were running.
- List active and closed network connections.
- View internet history (IE).
- Identify files on the system and retrieve them from the memory dump.
- Read the contents of notepad documents.
- Retrieve commands entered into the Windows Command Prompt (CMD).
- Scan for the presence of malware using YARA rules.
- Retrieve screenshots and clipboard contents.
- Extract hashed passwords.
- Retrieve SSL keys and certificates.
- And lots more!
Features
It supports investigations of the following memory images:
Windows:
- 32-bit Windows XP (Service Pack 2 and 3)
- 32-bit Windows 2003 Server (Service Pack 0, 1, 2)
- 32-bit Windows Vista (Service Pack 0, 1, 2)
- 32-bit Windows 2008 Server (Service Pack 1, 2)
- 32-bit Windows 7 (Service Pack 0, 1)
- 32-bit Windows 8, 8.1, and 8.1 Update 1
- 32-bit Windows 10 (initial support)
- 64-bit Windows XP (Service Pack 1 and 2)
- 64-bit Windows 2003 Server (Service Pack 1 and 2)
- 64-bit Windows Vista (Service Pack 0, 1, 2)
- 64-bit Windows 2008 Server (Service Pack 1 and 2)
- 64-bit Windows 2008 R2 Server (Service Pack 0 and 1)
- 64-bit Windows 7 (Service Pack 0 and 1)
- 64-bit Windows 8, 8.1, and 8.1 Update 1
- 64-bit Windows Server 2012 and 2012 R2
- 64-bit Windows 10 (including at least 10.0.14393)
- 64-bit Windows Server 2016 (including at least 10.0.14393.0)
Mac OSX:
- 32-bit 10.5.x Leopard (the only 64-bit 10.5 is Server, which isn’t supported)
- 32-bit 10.6.x Snow Leopard
- 32-bit 10.7.x Lion
- 64-bit 10.6.x Snow Leopard
- 64-bit 10.7.x Lion
- 64-bit 10.8.x Mountain Lion
- 64-bit 10.9.x Mavericks
- 64-bit 10.10.x Yosemite
- 64-bit 10.11.x El Capitan
- 64-bit 10.12.x Sierra
- 64-bit 10.13.x High Sierra
- 64-bit 10.14.x Mojave
- 64-bit 10.15.x Catalina
Linux:
- 32-bit Linux kernels 2.6.11 to 5.5
- 64-bit Linux kernels 2.6.11 to 5.5
- OpenSuSE, Ubuntu, Debian, CentOS, Fedora, Mandriva, etc.
Volatility supports a variety of sample file formats and the ability to convert between these formats:
- Raw/Padded Physical Memory
- Firewire (IEEE 1394)
- Expert Witness (EWF)
- 32- and 64-bit Windows Crash Dump
- 32- and 64-bit Windows Hibernation (from Windows 7 or earlier)
- 32- and 64-bit Mach-O files
- Virtualbox Core Dumps
- VMware Saved State (.vmss) and Snapshot (.vmsn)
- HPAK Format (FastDump)
- QEMU memory dumps
- LiME format
How to install Volatility?
Official Link – https://www.volatilityfoundation.org/releases
Github Link – https://github.com/volatilityfoundation/volatility
So you can download volatility from the above link and install it.
Because it’s a python tool, so you can run the tool with normal python command by downloading the source code from GitHub.
Step By Step Official Installation Guide – https://github.com/volatilityfoundation/volatility/wiki/Installation
Basic Commands of Volatility
We can see the help list of the tool by typing volatility -h. If you have installed it from source code type python vol.py -h for the help menu.
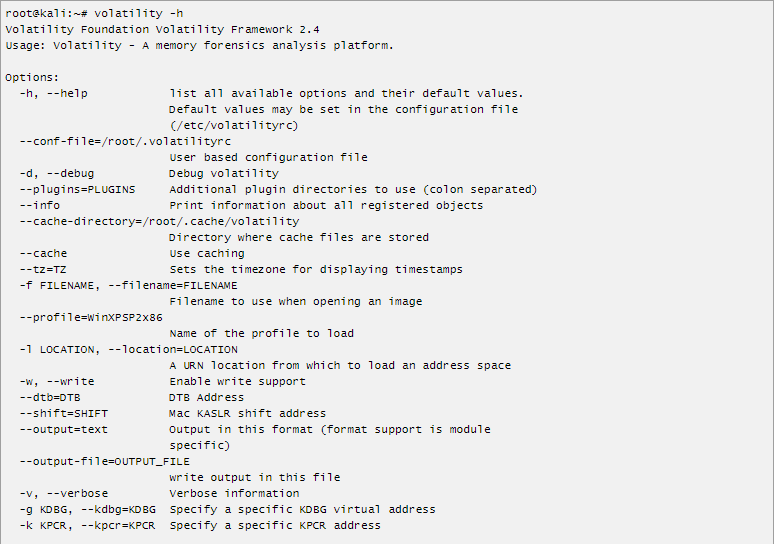
Basic Commands
volatility -f someimage.img imageinfo (It’s volatility2 command)
python3 vol.py -f someimage.img windows.info.Info (It’s volatility3 command)
The above command provides suggested profile information and other information like processor and architecture version of the memory.
Vol 3 commands for process listing
python3 vol.py -f file.dmp windows.pstree.PsTree # Get processes tree (not hidden) python3 vol.py -f file.dmp windows.pslist.PsList # Get process list (EPROCESS) python3 vol.py -f file.dmp windows.psscan.PsScan # Get hidden process list(malware)
Vol 2 commands for process listing
volatility --profile=PROFILE pstree -f file.dmp # Get process tree (not hidden) volatility --profile=PROFILE pslist -f file.dmp # Get process list (EPROCESS) volatility --profile=PROFILE psscan -f file.dmp # Get hidden process list(malware) volatility --profile=PROFILE psxview -f file.dmp # Get hidden process list
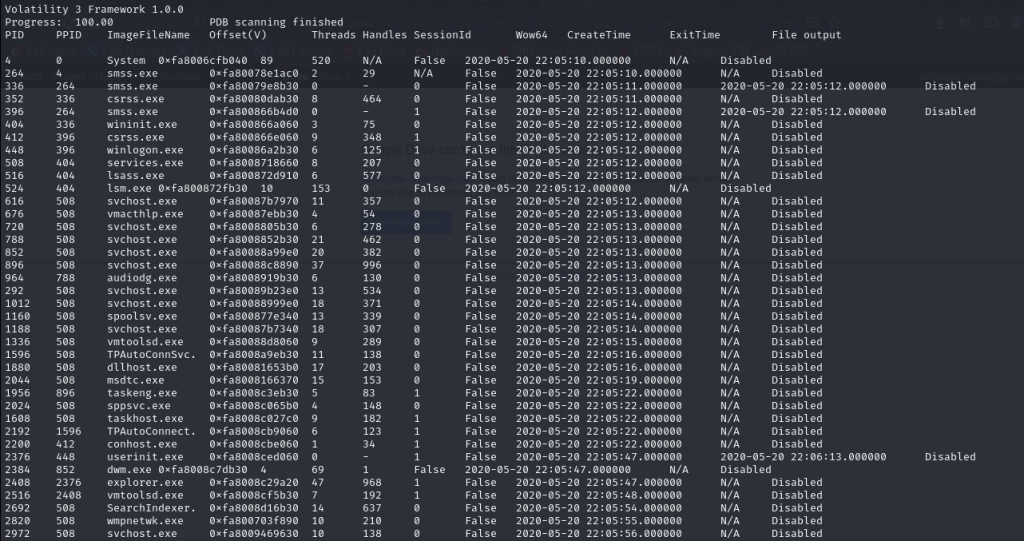
The process dump will look like the above image.
There are lots of commands and flags in volatility and it’s nearly impossible to incorporate all the commands in one blog.
You can check all the commands here.
Some memory images are listed below in the additional resource section. So that you can practice volatility on your own.
Additional Resources
Volatility Memory Sample – https://github.com/volatilityfoundation/volatility/wiki/Memory-Samples
Volatility Commands – https://book.hacktricks.xyz/forensics/basic-forensic-methodology/memory-dump-analysis/volatility-examples#volatility-commands
Volatility Cheatsheet – https://downloads.volatilityfoundation.org/releases/2.4/CheatSheet_v2.4.pdf
For more blogs like this visit our blog page








