FortiGuard Labs is a threat intelligence and research organization at Fortinet. It is comprised of experienced threat hunters, researchers, analysts, engineers, and data scientists. Its mission is to provide customers with the industry’s best threat intelligence to protect them from malicious cyberattacks. The researchers at FortiGuard Labs have discovered a new ransomware called Diavol. And they suspect Wizard Spider, the cybercrime group to be behind it, this was also the group that was behind the Trickbot botnet.
Upon analysis, it was found that there was another ransomware that possessed similar properties like both used asynchronous I/O operations for file encryption, using virtually identical command-line parameters for the same functionality i.e. logging, drives, and network shares encryption, network scanning. However, no direct link could be established.
There’s also no evidence of data exfiltration capabilities before encryption in the case of Diavol Ransomware, a common tactic used by ransomware gangs for double extortion.
Capabilities:
The major difference between Diavol and other ransomware is that Diavol uses user-mode Asynchronous Procedure Calls (APCs) with an asymmetric encryption algorithm. This sets it apart from other ransomware families as they commonly use symmetric algorithms to significantly speed up the encryption process.
Diavol also lacks any obfuscation as it doesn’t use packing or anti-disassembly tricks, but it still manages to make analysis harder by storing its main routines within bitmap images.
When executing on a compromised machine, the ransomware extracts the code from the images’ PE resource section and loads it within a buffer with execution permissions.
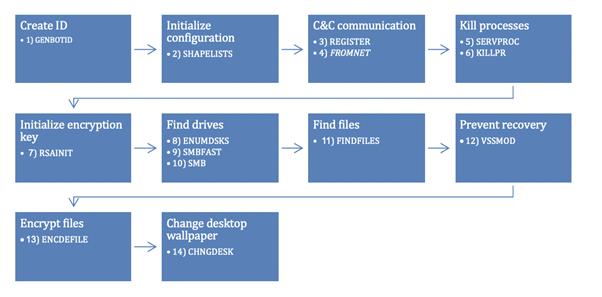
The code extracts amounts to 14 different routines that will execute in the following order:
- Create an identifier for the victim
- Initialize configuration
- Register with the C&C server and update the configuration
- Stop services and processes
- Initialize encryption key
- Find all drives to encrypt
- Find files to encrypt
- Prevent recovery by deleting shadow copies
- Encryption
- Change the desktop wallpaper
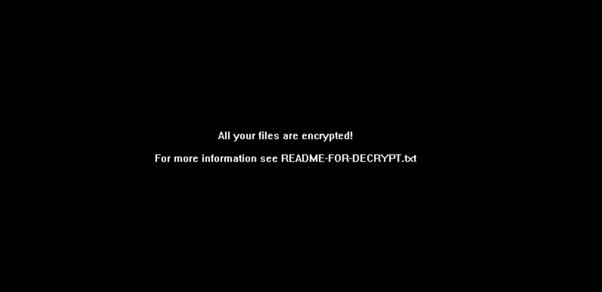
Just before the completion of Diavol ransomware, it changes each encrypted Windows device’s background to a black wallpaper with the following message: “All your files are encrypted! For more information see README-FOR-DECRYPT.txt”.
Fortinet’s Insight
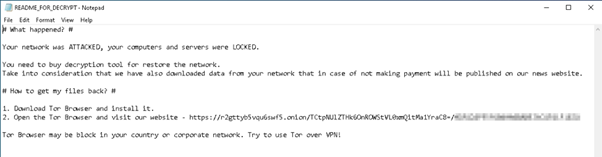
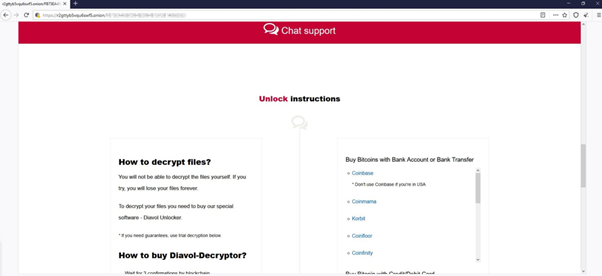
According to the note, the authors claim they stole data from the victim’s machine, though the researchers did not find a sample that was capable of performing that. This was either a bluff or a placeholder for future capabilities. Browsing to the URL led to us a website, seen in figures 2 and 3, from which we derived the name for the ransomware.
Although the Fortinet researchers suspect it to be an activity of Wizard Spider Group, no confirmations have been given as to what the source of the intrusion is. Fortinet says “The parameters used by the attackers, along with the errors in the hardcoded configuration, hint to the fact that Diavol is a new tool in the arsenal of its operators which they are not yet fully accustomed to.”
Also “As the attack progressed, we found more Conti payloads named locker.exe in the network, strengthening the possibility the threat actor is indeed Wizard Spider. Despite a few similarities between Diavol, Conti, and other related ransomware, it’s still unclear, however, whether there’s a direct link between them. And, there are a couple of major differences from attacks previously attributed to Wizard Spider & Co., namely:
– No checks and balances to ensure the payload will not execute on Russian victims.
– No clear evidence of double extortion in the environment was found.”
Trickbot impact on Enterprise
The Trickbot botnet as mentioned earlier is operated by the Russian-based financially motivated cybercrime group called Wizard Spider. The botnet is used to drop second-stage malware on compromised systems and networks.
Trickbot has some serious impacts on enterprises since it propagates through corporate networks. If it gets admin access to a domain controller, it tends to steal the Active Directory database to collect even more network credentials the group can use to make their job easier.
Although Microsoft and several partners announced the takedown of some Trickbot C2s after the US Cyber Command also reportedly tried to cripple the botnet, TrickBot is still active, with the group still releasing new malware builds.
The TrickBot gang’s operations entered a higher gear during the summer of 2018 when they started targeting corporate networks using Ryuk ransomware and again in 2020 after switching to Conti ransomware.
The developers of Trickbot have also started deploying the stealthy BazarLoader backdoor in attacks in April 2020, a tool designed to help them compromise and gain full access to corporate networks before deploying the ransomware payloads.
References: https://www.fortinet.com/blog/threat-research/diavol-new-ransomware-used-by-wizard-spider








